Last updated: January 14, 2024
Don’t be alarmed if you find the following document quite complex and heavily packed with technical details. That’s the way it was designed to be. Our aim is to provide not just a superficial overview, but the most comprehensive insight into the principles guiding our work and the specifics of how our processes are structured. To make the technical content more accessible, we have interspersed it with quotes from our team members, similar to the one you’re reading now.
Introduction
Mission
Q: What is the primary objective of our blog/website?
The main objective of HandyRecovery.com is to serve as a comprehensive resource for regular home users seeking to recover their lost data, address all popular OSes (iOS / Android / macOS / Windows / Linux) issues, and optimize their storage solutions in a straightforward and cost-efficient manner.
Q: How do we aim to accomplish our primary objective?
HandyRecovery.com achieves its mission with our innovative Data Recovery Solver Engine and our comprehensive, expert-written content.
At the heart of HandyRecovery.com lies our unique Data Recovery Solver Engine, which is designed to simplify the data recovery process by offering an intuitive interface that guides users through a series of questions to diagnose their data loss scenario and provides a customized solution to recover lost files efficiently and effectively.
Our website also hosts an extensive library of articles, guides, and tutorials on all aspects of data recovery. Each piece of content is written to educate our readers on a wide array of topics that extend beyond DIY data recovery strategies for various devices. For example, we provide authoritative advice on data loss prevention, maintaining data integrity, and increasingly, optimizing Apple storage solutions.
Q: What niche or audience do we primarily cater to?
HandyRecovery.com is primarily designed for home users, and everyone who might not care about deep technical knowledge, but still encounter various technology-related challenges. “Challenges” including – but not limited to – data loss. As such, we concentrate on delivering dependable and comprehensive information, presented in a manner that is accessible to all. Our content covers a broad spectrum of topics, ranging from data recovery to storage optimization and troubleshooting, for platforms like iOS, macOS, Windows, and more.
Our Authors
Q: Who are our authors, and what qualifications do they possess?
Our authors at HandyRecovery.com are a diverse group of carefully selected individuals who share deep expertise in technology, with a specialized focus on data recovery, digital storage solutions, and operating system troubleshooting. Whether they are on our permanent staff or contributing as freelancers, each author has demonstrated a proven track record of technical proficiency and a talent for making complex topics understandable to a general audience.
Q: Are you looking for new talent to bring new perspectives to HandyRecovery.com?
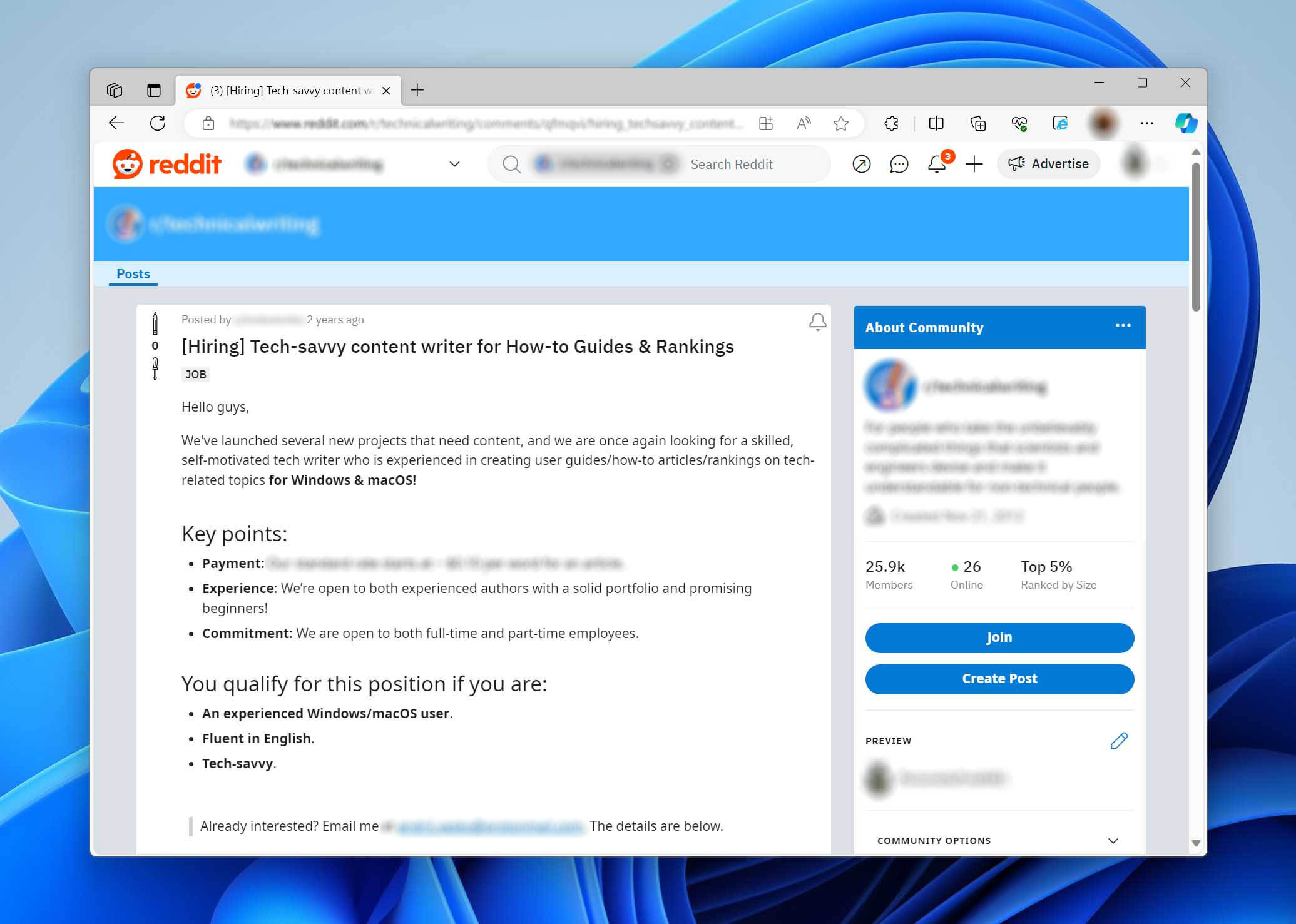
Absolutely, HandyRecovery.com is continually on the lookout for new talent. We believe that fresh perspectives can invigorate our content and bring new insights to the world of data recovery, data loss prevention, and data management. If you have a strong background in technology, especially with a focus on data recovery, demonstrable writing skills, and the ability to translate technical information into content that’s engaging and easy to understand, we want you on our team. For more details, read our About Us page.
Q: How does our hiring process cultivate the credibility and expertise of our writing team?
Our hiring process consists of multiple stages, beginning with a series of comprehensive test assignments that evaluate a candidate’s technical knowledge, writing prowess, and ability to align with our user-centric approach to content. The candidates’ submissions are meticulously reviewed by a panel that includes our senior content supervisor, who is responsible for maintaining editorial excellence, and our quality assurance (QA) technician, who verifies the technical accuracy and relevance of the information provided.
Candidates who successfully pass these tests enter a probation period. During this time, they work closely with our editorial team on actual content that will be published on HandyRecovery.com’s site. This on-the-job evaluation is a final test of their ability to maintain our high standards consistently and respond to editorial feedback constructively.
Only upon satisfactory completion of this period are they fully welcomed into our fold as trusted, verified authors capable of contributing to HandyRecovery.com’s mission.
It’s worth keeping in mind that top-tier content doesn’t appear auto-magically out of thin air. There’s no secret sauce for creating the articles and guides on HandyRecovery.com that others try to imitate (and glorified chatbots use as their training material for anything related to storage recovery). It takes advanced planning, thorough research, and rigorous testing for all our wordsmiths, staff writers, and contributors to craft articles of the highest possible quality. Then, our lead writers, editors, and technical overseers pore over them with a magnifying glass to vouch for their factual accuracy, technically accurate, engaging, and digestible. Still, if you put in the effort and follow our guidelines, it should be smooth sailing.
Brand Voice
Q: How would you describe the overall tone and style of HandyRecovery.com’s brand voice?
Our brand voice is approachable and concise because we want to be accessible to as many readers as possible, regardless of their technical background. We structure our articles to flow logically so that they are easy to navigate. Elements like FAQs, bullet points, and subheadings break up the text and make the information more digestible.
Q: How do we handle technical terms and complicated concepts in our content?
We avoid complicated language and unnecessary jargon. When we use technical terms or acronyms, we always explain them so that even those new to the topic can understand. We also recognize that some technical concepts require more than just a brief explanation. In such cases, we dedicate entire in-depth articles to these topics, providing comprehensive coverage that covers their nuances. A good example of this is our quick vs full format explainer article.
Q: What role do visual elements like screenshots play in our brand voice?
Visual elements, particularly screenshots, are integral to our brand voice. They serve as practical tools to illustrate and clarify our content, making it more engaging and easier to follow. We always create original screenshots on our own devices because we want them to be up to date and accurate.
Q: How do we incorporate a personal touch in our content?
We encourage our authors to infuse their personal experiences into their writing. Their personal insights, anecdotes, or practical tips infuse our content with authenticity and relatability. They help build a stronger connection with our readers by presenting real-life applications and experiences.
Q: How do we use inclusive and non-sexist language in our content?
We are committed to using language that is inclusive and free of gender or cultural biases. This means avoiding gender-specific terms when addressing or describing users, such as using “they” or “users” instead of “he” or “guys.” In technical descriptions, we replace outdated and potentially insensitive terminology with more modern and neutral terms.
Content Standards
Q: What standards do our authors adhere to when writing and submitting their content?
Authors at HandyRecovery.com are expected to adhere to the highest standards of quality and integrity in their writing. This includes a commitment to creating informative and accurate content that is also accessible and engaging for our audience. Every article must be well-researched, citing up-to-date and reputable sources, and provide genuinely useful actionable insights to our readers. We encourage a style that is clear, concise, and free of technical jargon unless explained thoroughly.
However, as we already stated, adhering to our guidelines and writing rules doesn’t limit each writer’s “voice”. On the contrary, we encourage a personalized approach and support taking alternative paths (where relevant), like writing in the first person. In many cases, this freedom is the spice that elevates our content.
In addition to providing essential information, we strive to offer unique perspectives and insights not commonly found elsewhere, adding depth and value to our content. Moreover, we maintain a strict policy that our editorial integrity is not for sale because we want our content to remain unbiased and trustworthy. Before submission, all content undergoes a rigorous review by our lead writer (who checks for clarity, grammar, and adherence to our style guide) and one of our technical experts (who guarantees the accuracy and relevance of the information).
Q: How do we guarantee originality and prevent plagiarism in our content?
Our authors are expected to produce content that comes from a place of original thought and deep understanding of the subject matter. To prevent plagiarism, all work must be the author’s own, and proper attribution must be given for any direct quotes or paraphrased content. While we are confident in the originality of our content, we take extra precautions by utilizing tools such as SEMrush’s Plagiarism Checker and Duplichecker to check for missing sources, quotation marks, and other similar issues, particularly when working with new authors who are still on probation.
Q: How do we avoid creating duplicate content when, for example, describing the same solutions to different problems?
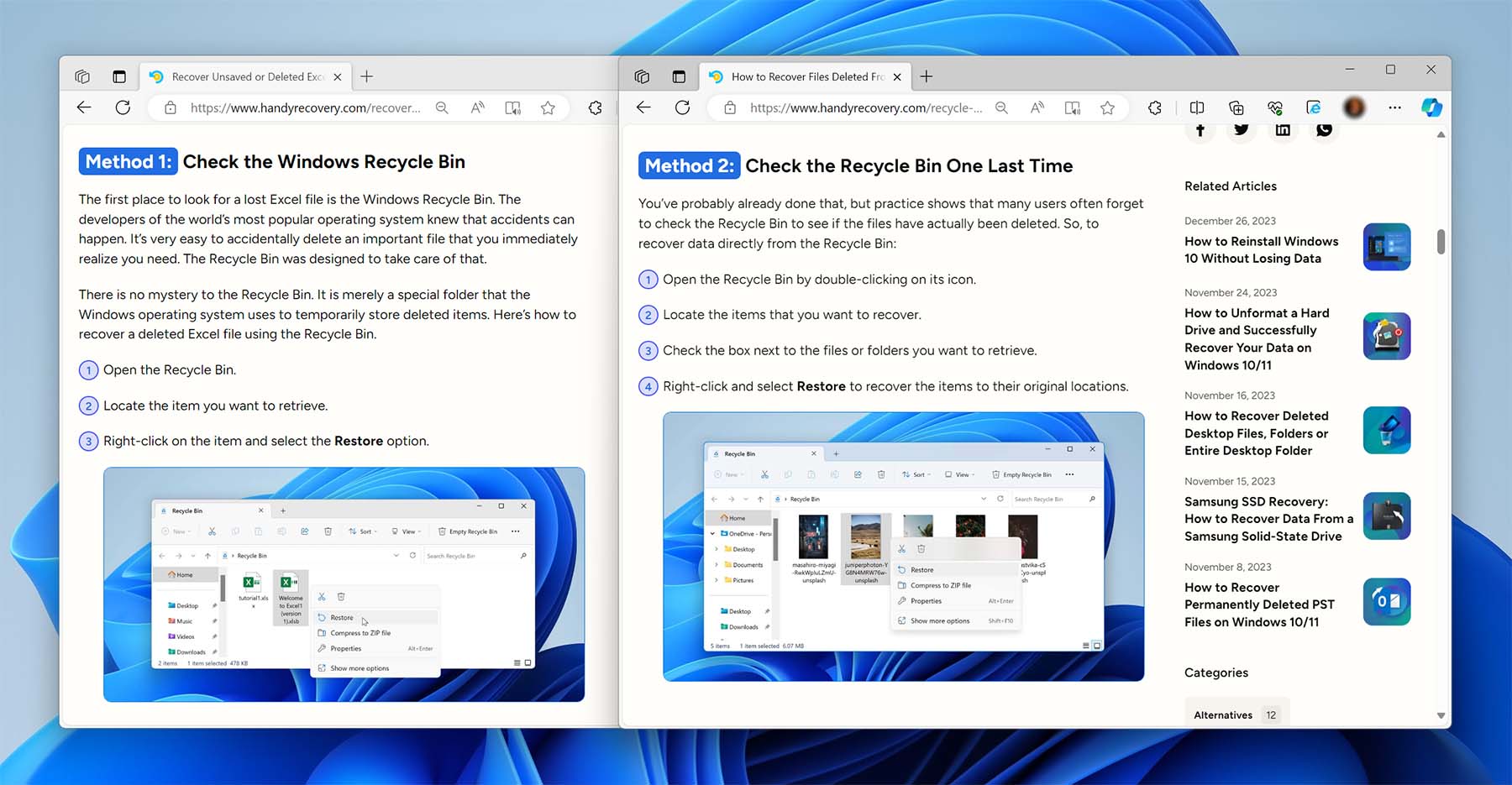
Certain data recovery instructions and methods are standard and may naturally recur across various articles. We don’t see this as inherently problematic, but we are mindful of tailoring mention of a method to fit the unique context in which it appears. This customization not only enhances the originality of each article but also provides our readers with precise and relevant guidance for their diverse technological needs.
Content Creation Process
Types of Content
Q: What are the different types of content we produce?
Our content includes detailed software ratings, in-depth software reviews, comprehensive software comparisons, and step-by-step how-to guides. These guides are carefully crafted to provide solutions that utilize a combination of innovative tools, software, and methods, including the native functions of various operating systems.
Q: What are the specific requirements and standards for each type of content?
Our content creation is governed by a rigorous set of standards so that every piece we publish meets the highest quality benchmarks. Here are the main requirements for each type of content:
- Ratings and Listicles: Our ratings and listicles are curated to feature only the top-tier software suited for specific data recovery, data loss prevention, and data management tasks. Each recommended software is tested and researched extensively to confirm its efficacy. We maintain the accuracy of details such as pricing and system requirements with regular updates so that our readers have the latest information at their fingertips.
- Reviews: Our review process is grounded in an extensive testing protocol designed to provide precise, verifiable insights into various critical software facets. These include effectiveness in the designated function, whether it be data recovery or file organization, user interface intuitiveness, algorithm accuracy, the breadth of features offered, and the software’s overall value proposition.
- How-to Guides: Our how-to content reflects our dedication to practical, user-friendly guidance. We scrutinize the software and methods recommended and structure our guides to follow an intuitive, logical progression. A key component of our advice is to offer effective, no-cost alternatives wherever possible, giving users a full spectrum of options.
Q: Do we collaborate with third parties for specific content pieces?
Consistent with our editorial independence, we do not engage in collaborations with any third parties when producing content. This approach guarantees that all information presented on HandyRecovery.com is free from external biases and aligns with our dedication to objectivity and reader trust.
Q: How do we maintain consistent use of American English in our content with a global team of writers?
We encourage our diverse, global team of writers to write in American English to maintain consistency across our content. We provide them with comprehensive style guides that outline the nuances of American English usage. Additionally, our editors meticulously review and edit articles, making necessary adjustments to align with American English.
Q: Do we use AI-generated content in our articles?
We like to always stay abreast of the latest technological trends, including AI but do not use or rely on AI-generated content for our articles. Our commitment is to original, human-authored content that reflects deep understanding and expertise in the field of data recovery and technology. AI tools may be used to assist in tasks like organizing information, processing data, or proofreading, but the core of our content creation process remains firmly in the hands of our skilled human authors.
In simpler terms, our philosophy regarding the use of AI is based on the principle that AI is first and foremost an assistant, not a replacement. In the marketing department, for instance, we often use AI to process large amounts of data more rapidly and efficiently. We also don’t mind if authors seek inspiration and AI assists them in generating ideas, or even in checking texts for grammatical errors. Again, for us, AI is primarily an assistant for routine tasks.
Our Testing Process
Software Testing
Q: How do we select software for testing?
The selection of software for testing at HandyRecovery.com is guided by a blend of popularity and efficacy. We lean towards software that not only draws the attention of a larger audience due to its prevalence but also those hidden gems that are highly effective yet may not be as well-known. Our editorial focus is to spotlight software that excels in tackling specific data recovery, data loss prevention, and data management tasks, offering the best solution to our readers.
For a more in-depth look at our software testing process, visit our dedicated page.
Q: What criteria do we use to determine the quality of a tool or software?
At HandyRecovery.com, our evaluation of tools and software extends across the spectrum of data recovery, data loss prevention, and data management solutions. We apply a rigorous and comprehensive set of criteria to recommend the best options available, regardless of their specific function. These criteria include:
- Price: We consider the cost of the software and assess whether it provides value for money and fits within a range of budgets.
- Features: We examine the range and effectiveness of features provided and whether the software can efficiently perform its intended tasks.
- Usability: The ease of use is paramount; we prefer software that users of all skill levels can navigate without difficulty.
- Performance: Our tests gauge the efficiency and effectiveness of the software, prioritizing consistent and reliable performance in its designated role.
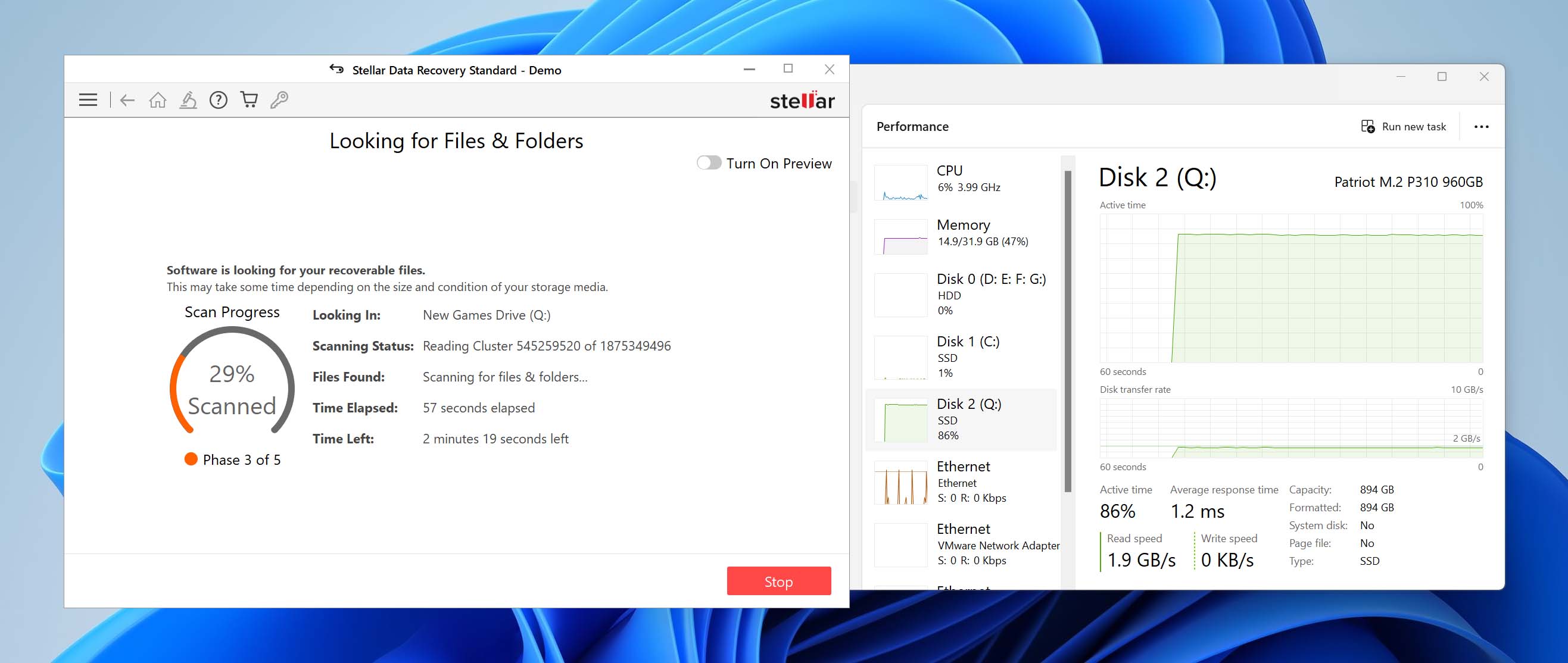
- Support and Updates: Because we want to recommend only software that can remain effective for a long time after purchase, we take into consideration customer support and regular updates.
- OS compatibility: The software’s compatibility with various operating systems is also a key factor. That’s because an application can receive support and regular updates and still be impossible to run on the latest version of Windows or macOS.
- User Feedback: We research reviews and testimonials from actual users published on review sites, discussion boards, and shopping websites to gauge satisfaction and identify any common issues.
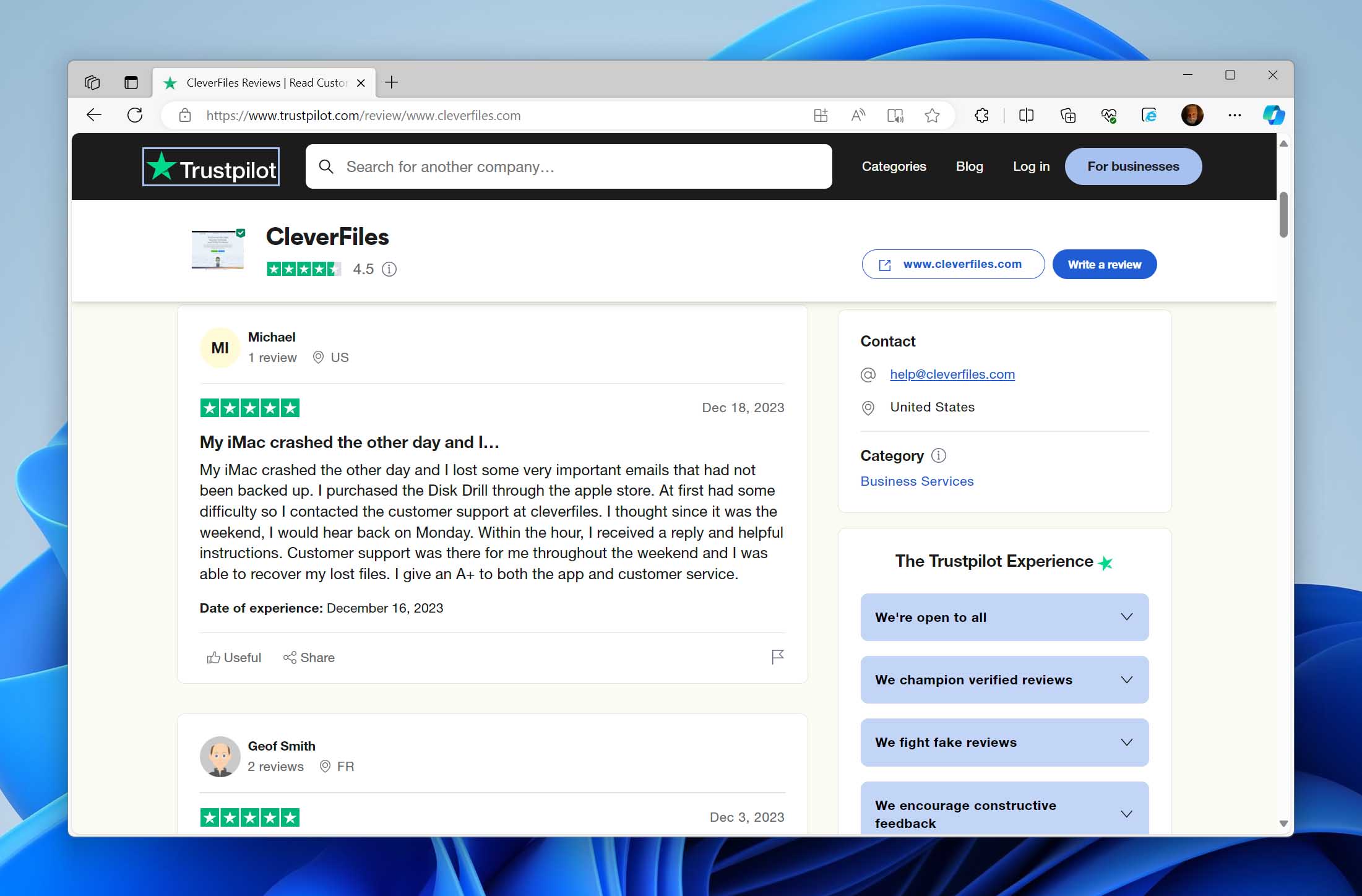
- Security: We carefully evaluate whether the software itself is safe and does not pose any risk to the user’s computer. Namely, we test if it is free from malware and does not compromise the integrity of the system.
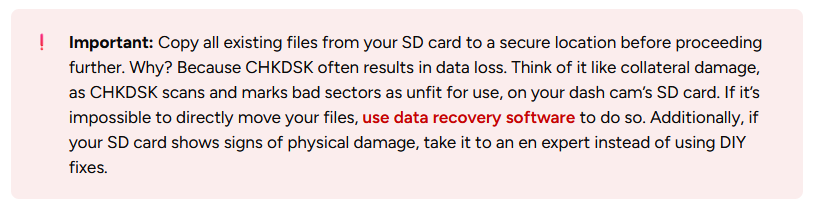
The Internet is littered with shoddy advice regarding data integrity, preservation, and recovery. However, there’s no need for such worries with our articles and guides. Is there even the tiniest chance a piece of software, method, or process could be destructive or have the potential to affect your data in any way? In such cases, we always make sure to add such a clarification and, whenever possible, a relevant accompanying screenshot. Like in this instance.
Non-Software Methods Testing
Q: How do we choose non-software methods to solve problems or provide guidance?
Our approach to selecting non-software recovery methods is rooted in professional knowledge and extensive research. We stay abreast of the techniques supported by operating systems like Windows, macOS, iOS, Android, and Linux and draw from our hands-on experience. This expertise directs us to methods that are effective, practical, and user-friendly for our audience.
Q: What tests or research are conducted to validate and evaluate these methods?
We undertake a comprehensive reevaluation of each method before inclusion in our content to guarantee the validity of our recommendations. We double-check that no outdated or subpar procedures are advised. Furthermore, we put new methods or tools through rigorous testing across various scenarios relevant to their intended use, guaranteeing that our recommendations stand up to real-world challenges and offer genuine utility to our users.
Crafting Our Articles
Q: How do our authors choose topics and conduct preliminary analysis or tests?
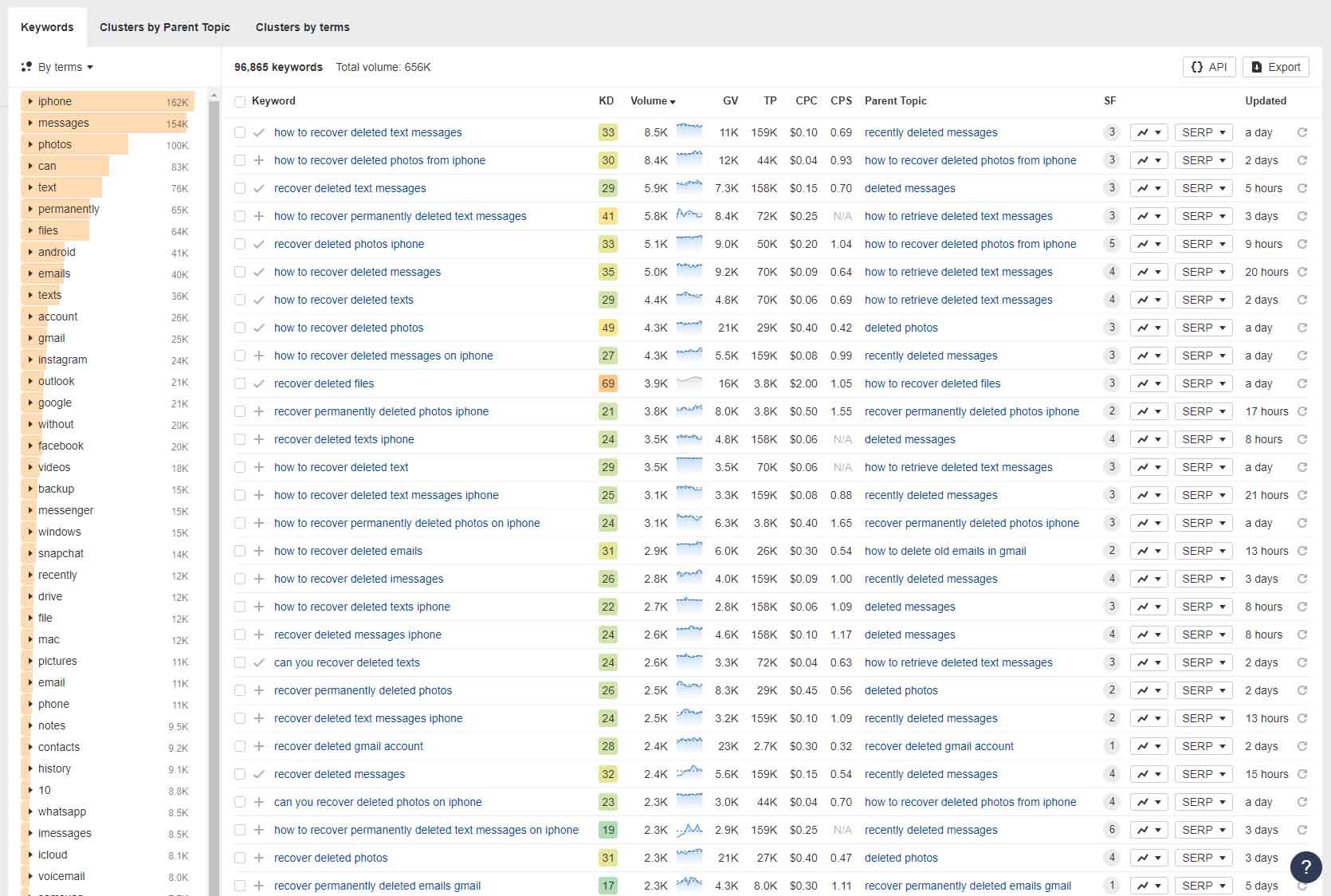
Our content and marketing team carefully curates topics based on their potential to draw readers and their connection to our existing content range. As a result, popular topics are covered, but there’s also a pathway for readers to deeply explore specific data recovery, data loss protection, and data management subjects. Once a topic is selected, our writers are tasked with conducting a thorough analysis or tests relevant to the subject to inform and enhance their articles.
As we mentioned on our ‘About Us‘ page, one of our main goals is to get 10,000 daily readers. To be honest, we can’t do this without focusing on topics that people find interesting and are searching for online. We use tools like Google Ads’ Keyword Planner, Ahrefs.com, and Google Trends, along with other resources, to find out what these topics are. We also look deeply into forums like Reddit, Superuser, and Quora, and check the ‘People Also Ask’ sections on Google to make sure we cover everything well. But it’s not just about writing articles that bring us more readers. Our collection of articles also includes a lot of pieces that help with very specific problems.
Q: What principles guide our writers in producing content that meets the standards of quality, depth, and relevance?
To uphold our standard of excellence, our writers abide by several key guidelines:
- Make sure all information is genuine and verifiable.
- Provide clear, practical guidance that readers can apply.
- Communicate ideas in an easily understandable way.
- Double-check facts to avoid errors and confirm grammatical precision.
- Scrutinize the nuances of topics to offer comprehensive insights rather than superficial coverage.
- Stay current with industry developments to deliver timely content.
These principles act as our compass, guiding writers to produce content that resonates with our readership and upholds the integrity of HandyRecovery.com as a trusted resource in the data recovery industry.
Q: How do our authors ensure that the content meets the needs and interests of our readers?
By keeping the reader at the forefront of our content strategy. Our authors engage with user feedback, follow the latest industry trends, and anticipate the questions and issues our readers may face. This reader-first approach allows us to produce content that resonates with our audience and their needs and interests.
Q: How do our authors structure content?
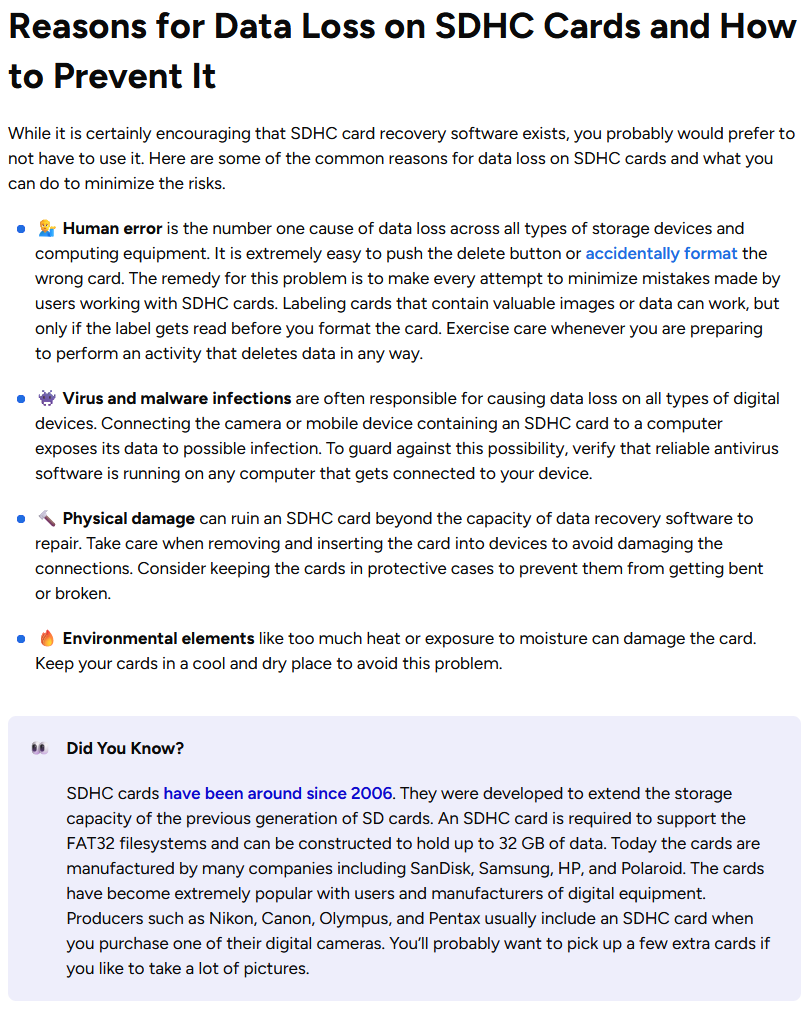
To keep our readers engaged, all of our content is carefully structured with readability in mind. Our authors break down information into logical sections that are separated by headings. This not only makes it so the text is formed into bite-sized, easy-to-read portions but also allows our readers to easily jump between different sections to find what they’re looking for. Additionally, our authors employ the use of numbered and bulleted lists, on-page styling, and tactful image placement to make sure the flow of text is smooth and natural.
By taking a deliberate and strategic approach to content structuring, we aim to capture and keep the attention of our readers. The example below demonstrates how we use different elements, like headings, bulleted lists, and on-page styling, to break up information. In doing so, we can guarantee that the information is presented in a visually appealing manner which is easy to follow without feeling too much like a boring, overly technical document.
Article Review and Quality Assurance
Q: What are the stages of our article review process?
Our article review process can be broken down into the following main stages:
- Article submission: Authors perform a thorough self-review to guarantee the article meets the initial requirements and our guidelines before submitting it for editorial review.
- Initial review by the editor who assigned the article: The person who assigned the article, our content strategy expert, conducts a preliminary check for basic compliance with the task directives.
- Second, more detailed editorial review: A more detailed inspection by a senior content supervisor takes place at this stage. We look at how the article flows, whether it’s well-structured, makes sense, and is complete in its coverage. Feedback is given on areas that need polishing.
- QA review: This step is all about the nitty-gritty. A quality assurance technician scrutinizes the usefulness and clarity of the content, especially the methods described. He also points out any additional insights or advice that might benefit the reader.
- Final review: Last but not least, the article undergoes a final check. This helps verify that all previous comments have been considered and the article is now in its best form, ready for publishing.
Q: What specific checklists or guidelines does each reviewer adhere to?
- Content Strategy Expert’s Review:
- General Article Review Steps:
- Check for a uniform tone and voice throughout the article.
- Make sure all parts of the topic are fully explored.
- Point out any clear oversights by the writer.
- Checking for Task Compliance:
- Validate that the article’s structure is logical, with well-crafted sections and headings.
- Cross-check the content against the brief to confirm all required points are covered.
- Include and distribute keywords naturally to make it easy for people who are dealing with data recovery issues to find the article via search engines.
- Confirm that the article includes relevant internal links to other content.
- General Article Review Steps:
- Quality Assurance Review:
- Technical Accuracy:
- Verify that the recovery methods are current and practical.
- Double-check that all technical details are accurate.
- Validate if the methods match with the article’s focus and target audience.
- Visual and Instructional Clarity:
- Analyze that screenshots directly illustrate the associated instructions.
- Consider if additional methods or short info sections with warnings or clarifications might be helpful.
- Technical Accuracy:
- CMS Publication Review:
- Pre-Publication:
- Make sure the article is saved and formatted in CMS correctly.
- Check that all formatting and styling options are applied correctly.
- Visual Presentation:
- Adjust design elements like color blocks or emojis to enhance readability.
- Ensure screenshots are the right size and of high quality.
- Validate the accuracy of technical commands and instructions against screenshots.
- Final Touches:
- Use a validator tool to check the article for any errors.
- Add screenshots where they can provide additional clarity.
- Make any necessary semantic corrections, such as fixing incorrect heading levels.
- Pre-Publication:
For screenshots, we first make sure they really match the topic of the article. We check that the methods we talk about work well in real situations and on actual devices. Also, the screenshots need to be the right size, format, and style.
Starting in 2022, we’ve been more careful with how we take screenshots and we’ve set new standards for quality. You might still see some older screenshots, but we’re updating all the screenshots on our website to meet these new standards.
Fact-Checking Policy
Sources and Verification
Q: What sources do we rely on for our information?
The content on HandyRecovery.com is built on a foundation of broad technological expertise and firsthand experience not only in data recovery but also in data loss prevention, and data management. Our experts draw on their comprehensive knowledge in these areas to provide reliable, tested advice. To support our firsthand insights, we consult primary, authoritative sources such as official documentation from technology providers like Microsoft and Apple. We also utilize trusted industry research portals for high-quality case studies and statistical data.
Q: How do we verify the authenticity and credibility of our secondary sources?
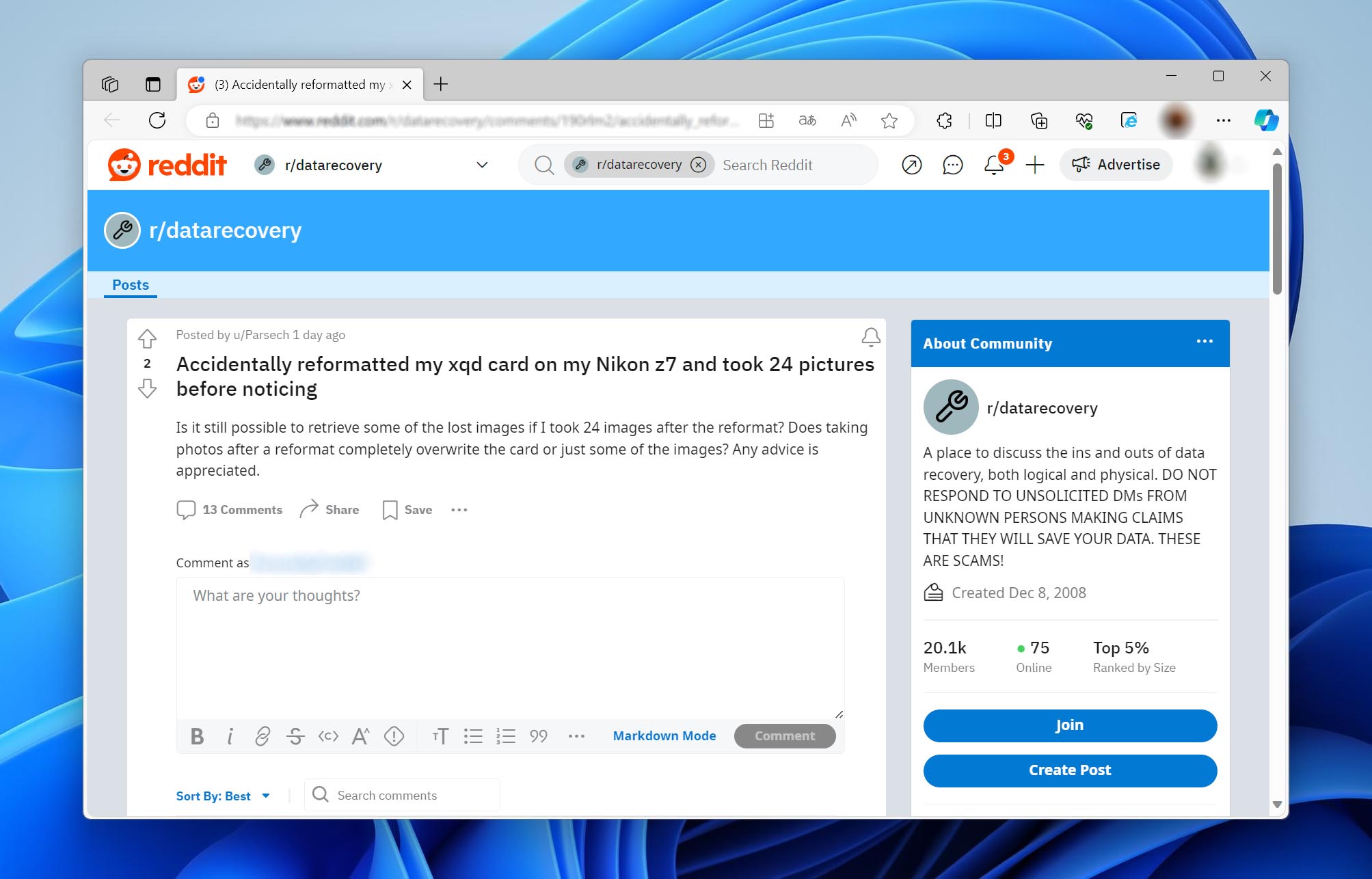
Our commitment to authenticity means that any secondary source we use must pass through a stringent verification process. This involves cross-checking the information with primary source material and, when possible, reproducing the scenarios to test the validity of the data recovery methods and techniques discussed. Our engagement with community-driven platforms and the often invaluable nuggets of information posted on sites like Reddit exemplify this practice—we critically assess each contribution and test it against both our firsthand experiences and authoritative sources.
Content Accuracy and Relevance
Q: How often do we review our content for accuracy and relevancy?
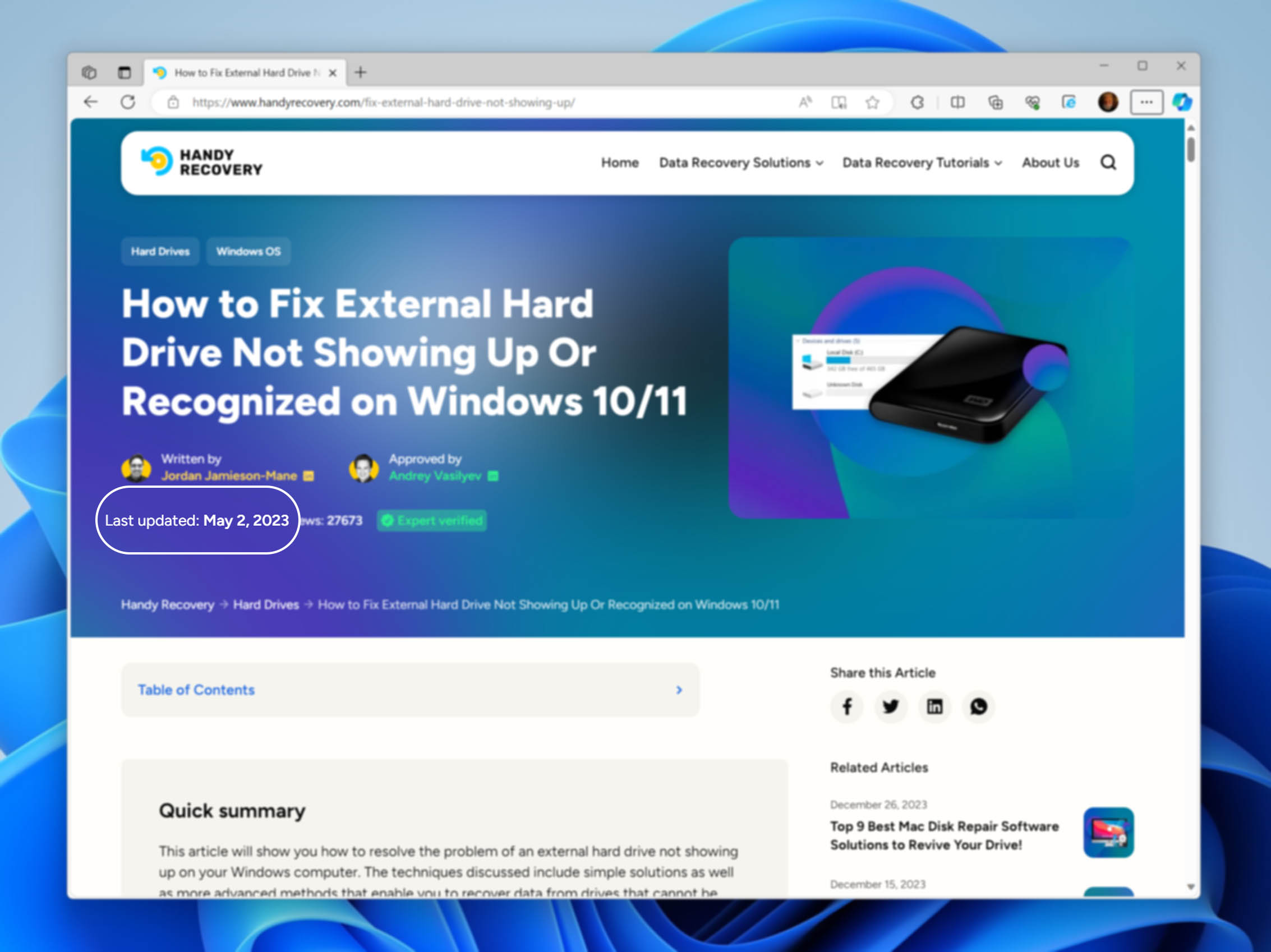
We are committed to keeping our content up to date, and in line with the most current industry developments and news. To maintain this standard, our articles undergo routine accuracy and relevancy reviews at set intervals. Based on the article’s importance and subject matter, reviews are scheduled at three different frequencies: every three months for rapidly changing topics, every six months for those with moderate updates, and annually for evergreen content.
Q: What triggers a manual content review outside of our regular review intervals?
While our scheduled reviews are comprehensive, certain situations prompt an immediate manual review to maintain our content’s integrity and usefulness. These triggers can include direct feedback from our readers highlighting potential issues, significant software updates for the solutions and platforms we discuss, or noticeable changes in Google search trends that reflect a shift in information relevance.
Corrections Policy
Error Identification and Reporting
Q: How do we handle errors or inaccuracies found in our content post-publishing?
At HandyRecovery.com, we prioritize the accuracy and dependability of our content. When an error is identified—whether internally or brought to our attention by readers—we act promptly to correct the issue. A dedicated task is created for the editorial team, and we strive to make the necessary corrections within the shortest possible timeframe to keep our content remains a trusted resource.
Q: What is our process for readers or users to report potential mistakes or inaccuracies?
We value our reader’s contributions to maintaining the integrity of our content. Users can report any potential errors or inaccuracies they come across by reaching out to us via our contact form or by sending us an email message (you can find both on the Contact Us page). When sending an email, we request that the subject line include “Correction Suggestion” to help us process the message with the appropriate priority.
Q: How do we communicate corrections or updates to our audience?
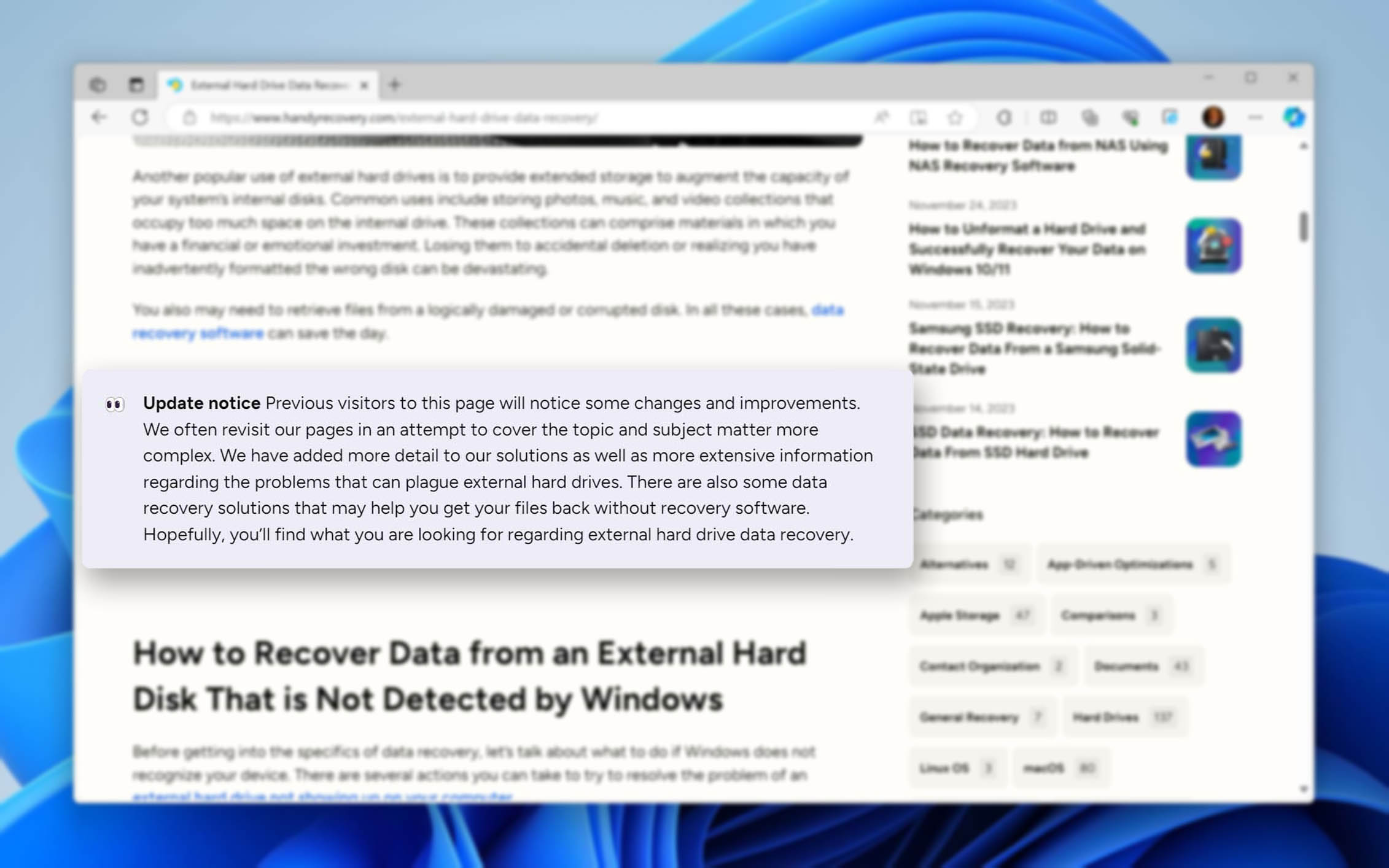
Whenever we make corrections or updates to our content, we clearly communicate the changes to our readers by including an “update notification” within the updated article. This notification highlights the date of the update and details the nature of the changes made.