The loss of encrypted data is more complicated than traditional data recovery, as you have to overcome the hurdle of recovering the data, as well as decrypting it. Due to the presence of encryption, some data recovery methods that would otherwise prove useful are ruled out, such as signature-based recovery.
Despite the complexities associated with recovering encrypted data, it is possible so long as all conditions are right. I’ll share some scenarios in which encrypted data loss commonly occurs and go over what options you have to recover encrypted files.
Common Cases of Encrypted Data Loss
I’d like to first discuss the different types of encrypted data loss you can come across, as each can vary greatly in how they handle data.
File deletion
File deletion refers to when the encrypted object, whether it be a volume, folder, or file, is deleted by the user or a program. In the case of file deletion, you perform encrypted data recovery using data recovery software. The same goes for programs that use files that act as virtual encrypted disks, like Veracrypt and DiskCryptor.
Your options:
Lost certificate
Encryption algorithms rely on certificates to access the data. Iaf you lose the certificate, recovering the data is almost impossible without a backup. After all, it is the key to the lock. Your only options in this case are finding the key or restoring from a backup. Even if you recover the data, it will still be encrypted and inaccessible.
Your options:
Accidental device formatting
Formatting is tricky. If you formatted the drive with the same file system it was already using, data recovery algorithms that utilize file system records won’t work because the old records have been overwritten. And, because the data was encrypted, signature-based scanning methods are useless. However, if you chose a different file system when formatting, you may have a chance of recovering the data using data recovery software.
Your options:
Ransomware attack
Ransomware is a form of malware. Once it has infected your computer, it encrypts the contents of your drive and then demands payment from you to restore access, typically through crypto. Even if you pay, there’s no guarantee you’ll even be given the decryption keys.
Your options:
5 Methods for Encrypted Files Recovery
Just like with regular data recovery, there is never a guarantee when it comes to recovering encrypted data. Regardless, the solutions I’ve included have proven useful in the past, either to myself or to other users who have experienced the problem.
Method 1: Locate the Required Certificates
Seeing as every method in this list is going to require the appropriate certificates to access the encrypted data, I’m putting this at the start as a kind of preliminary step. If you’ve lost your certificate, there are some places you can look to see if a backup is available. This depends on the type of encryption you’re using.
- BitLocker – When setting up BitLocker, it’s possible to attach your BitLocker Recovery Key to your Microsoft Account. Check your Microsoft account to find your BitLocker Recovery Key.
- NTFS with EFS – Not to be confused with BitLocker, the Encrypting File System (EFS) is included with the NTFS file system and provides optional filesystem-level encryption. The File Encryption Key (FEK) is stored in your user account. If, for any reason, the private key becomes lost, it may be possible to recreate another from an offline system, though the chances are slim and the process is very technical.
- APFS/HFS Encryption – APFS and HFS encryption involves using the user account password to decrypt files. Users are prompted to print or save the recovery key when setting it up. This recovery key can optionally be saved in iCloud.
Of course, there are many other encryption algorithms to consider, and each one may have its own way of storing backup keys and certificates. Regardless, without the correct recovery key, certificate, or password, your chances of accessing the recovered data are slim to none.
Method 2: Restore System or Files From a Backup
Restoring a copy of your data is always going to be the most reliable recovery method. Whether you need to restore individual files or your entire system, it’s stress-free so long as that data is available. If you don’t have a backup, skip ahead to the next method.
This method will only work if you already set up a backup schedule in the past, which has run successfully at least once. If you didn’t, move to the next recovery method.
The exact steps needed to restore your data will depend on what backup tool you’re using. I’m going to show you how to restore files from a File History backup in Windows:
- Click Start and type “File History”. Open it.
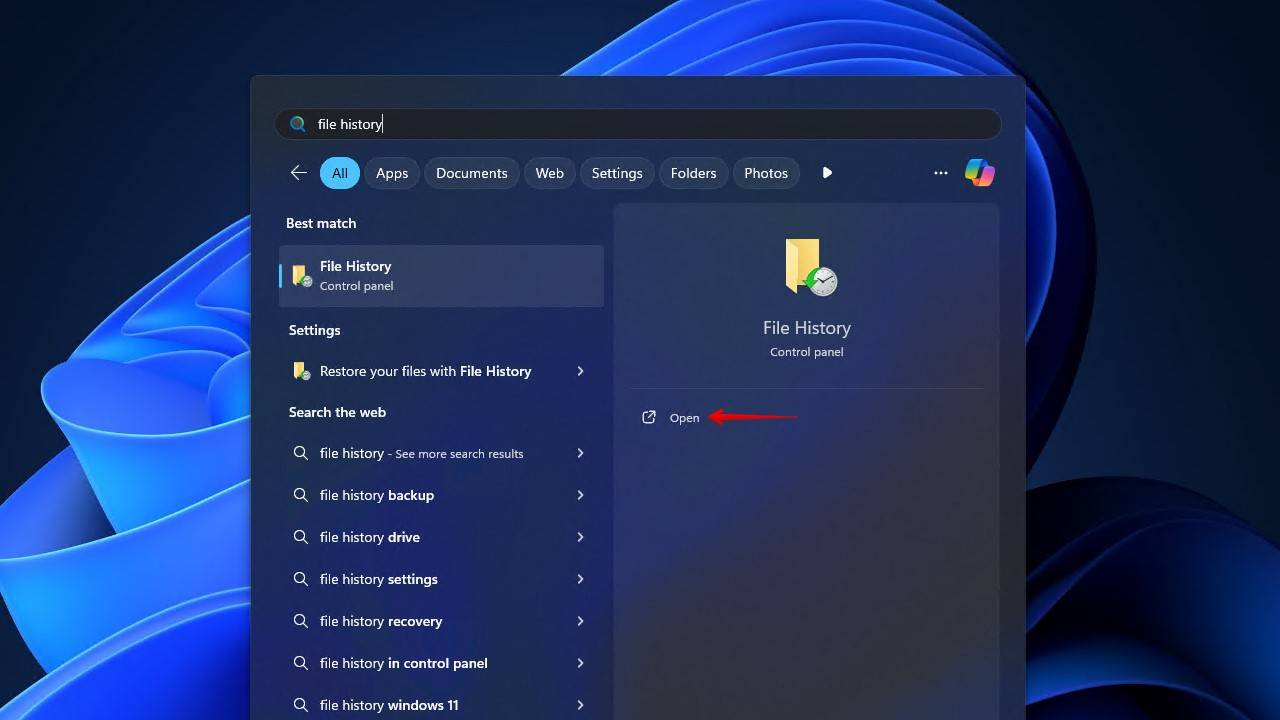
- Click Restore personal files.
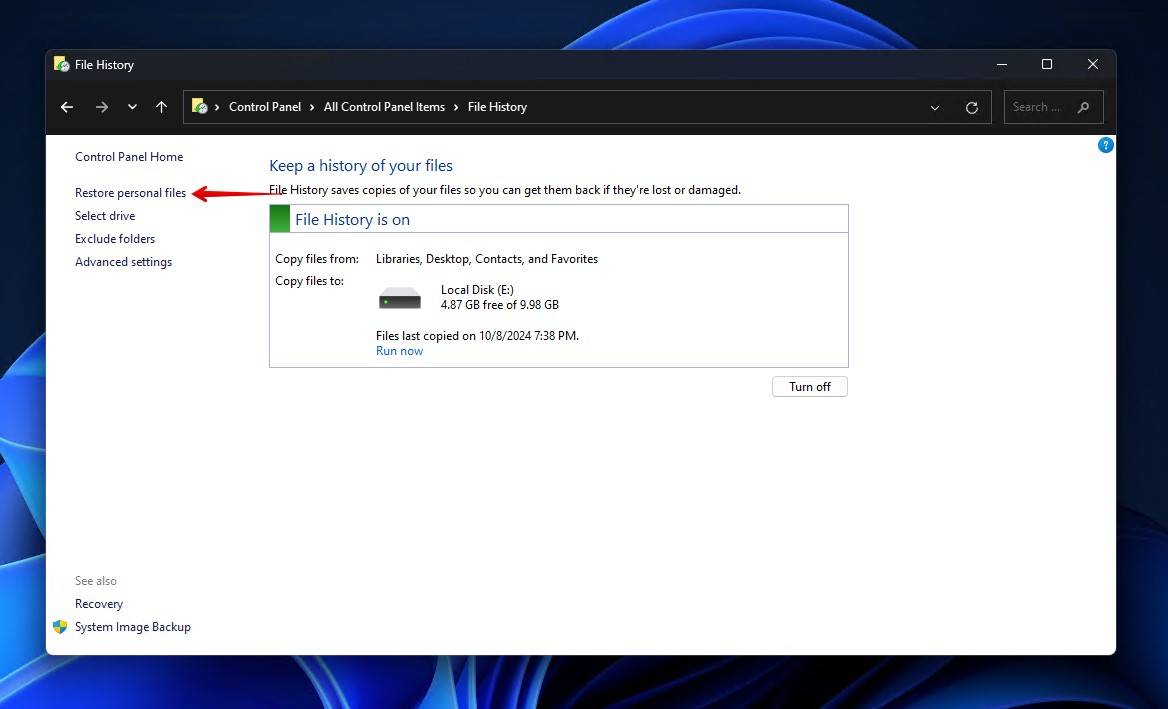
- Locate the files on the encrypted drive that you’d like to restore.
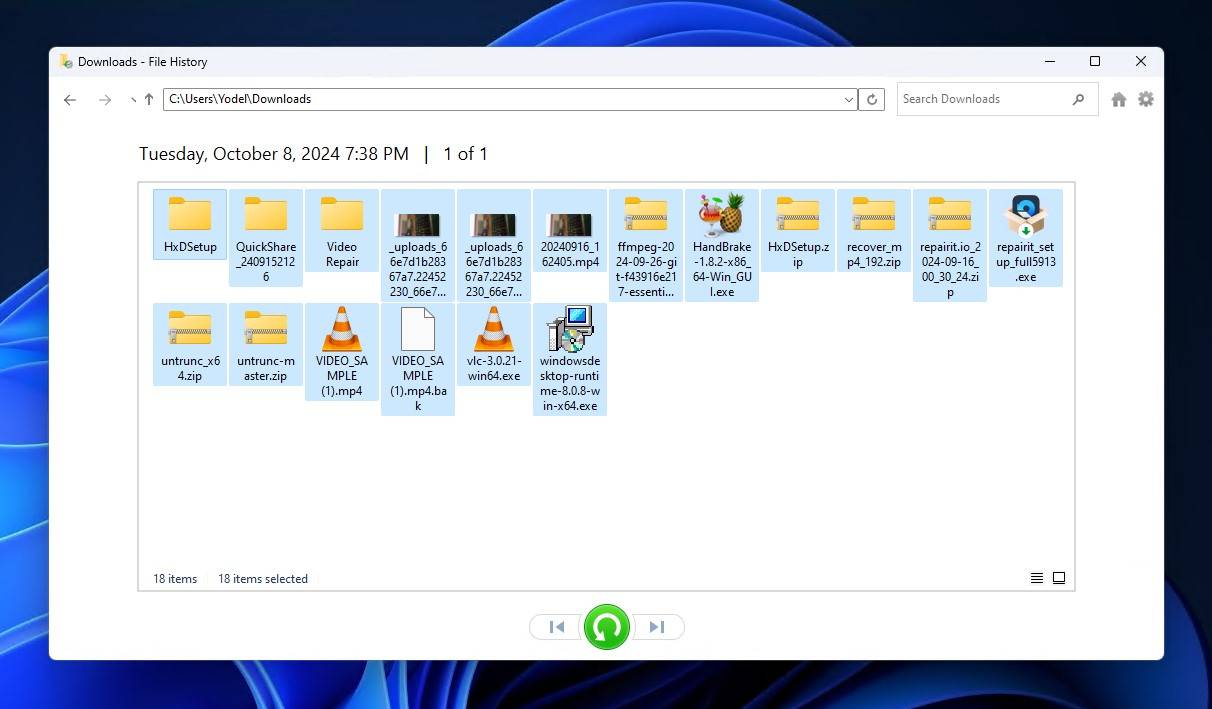
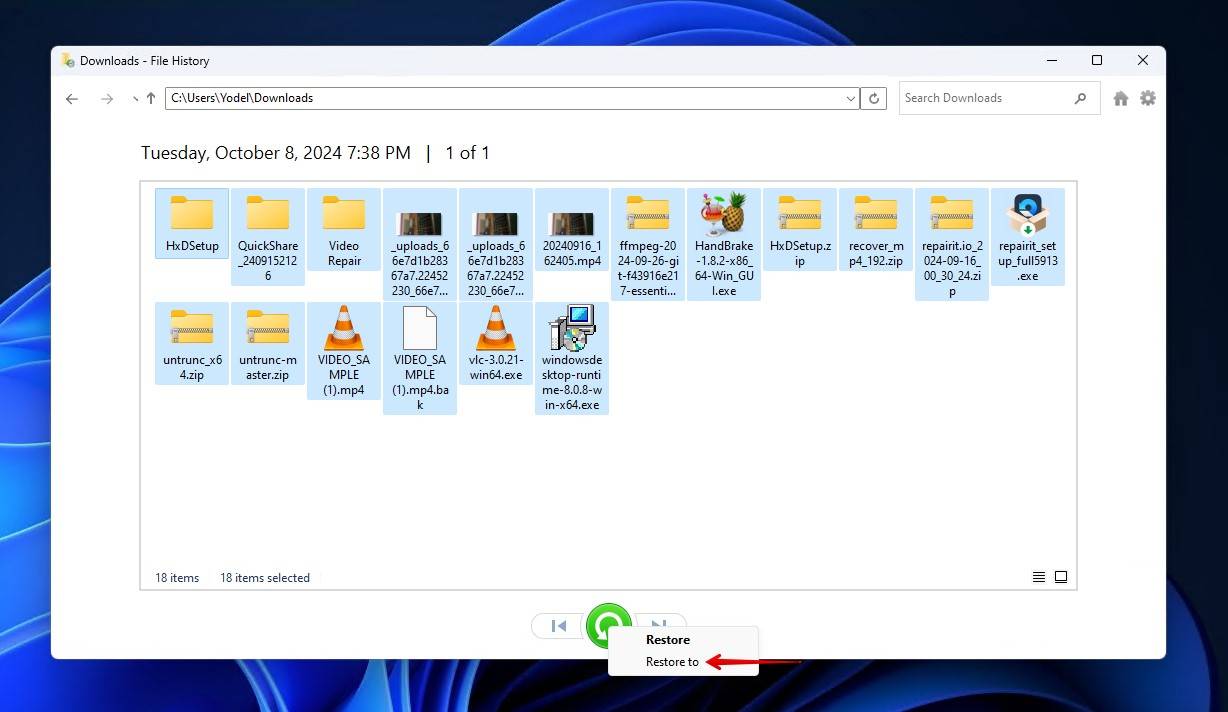
- Right-click the green Restore button and click Restore to.
Method 3: Recover Using Data Recovery Software
Recovering encrypted data with data recovery software is indeed possible, but only if (a) you have the correct credentials, and (b) the file system is still intact. Unlike traditional data recovery where files can be found using their unique file signature, encrypted files use a random data structure to obscure what the file contains. This means the only way to locate data is by utilizing the records from the file system.
Data recovery software is not a reliable way to recover any EFS-encrypted data that was deleted. Data recovered from an EFS-encrypted partition will still retain its encryption but with no possibility of decrypting its contents.
I’m going to demonstrate what the recovery process looks like with the recovery tool I prefer to use, Disk Drill. You can download Disk Drill and recover up to 500 MB for free.
Follow these steps to recover data from an encrypted drive using Disk Drill:
- Download and install Disk Drill.
- Select the encrypted drive and click Search for lost data. If the drive has not been decrypted in Windows, Disk Drill will now ask for the encryption password.
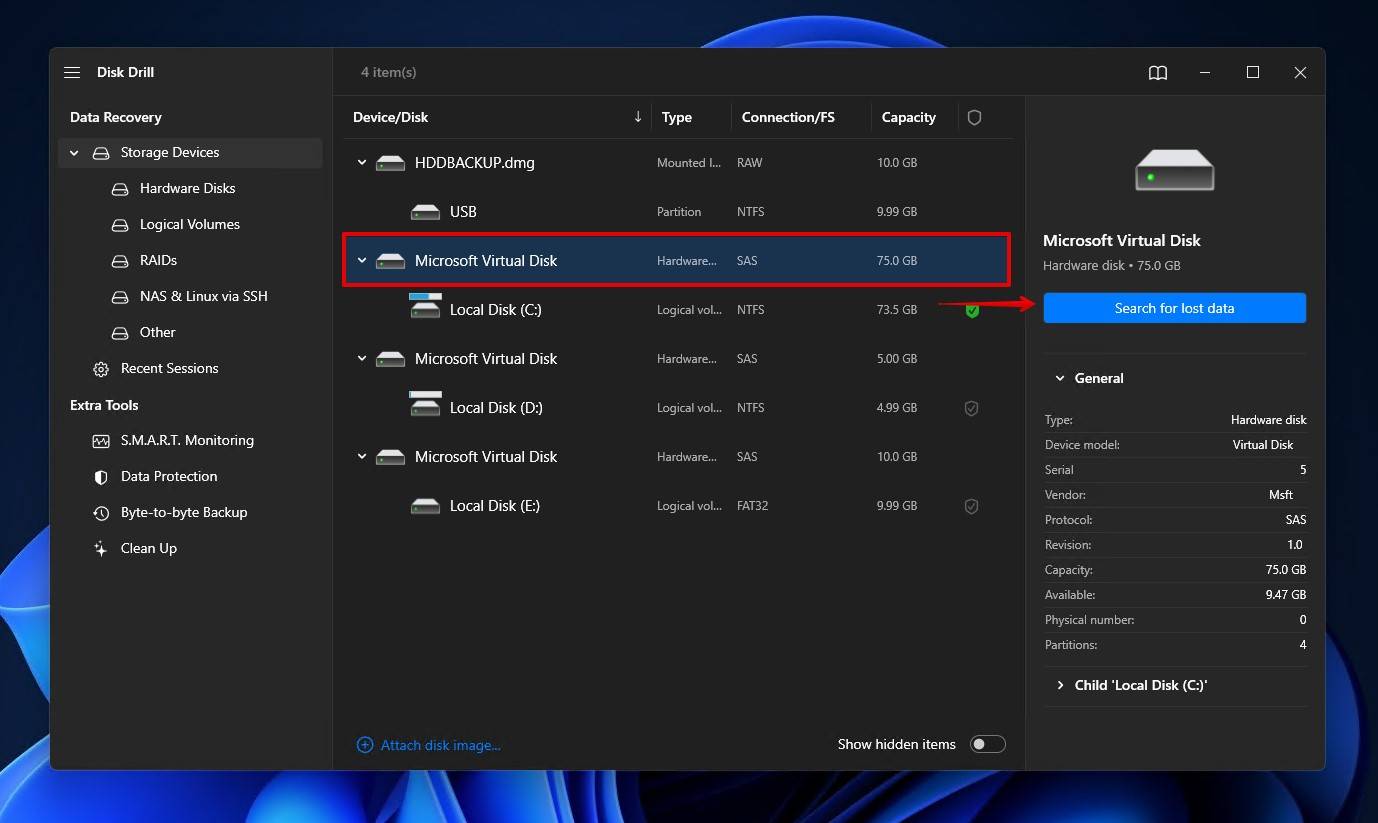
- Click Review found items. Alternatively, click one of the colored file type icons, or click Recover all.
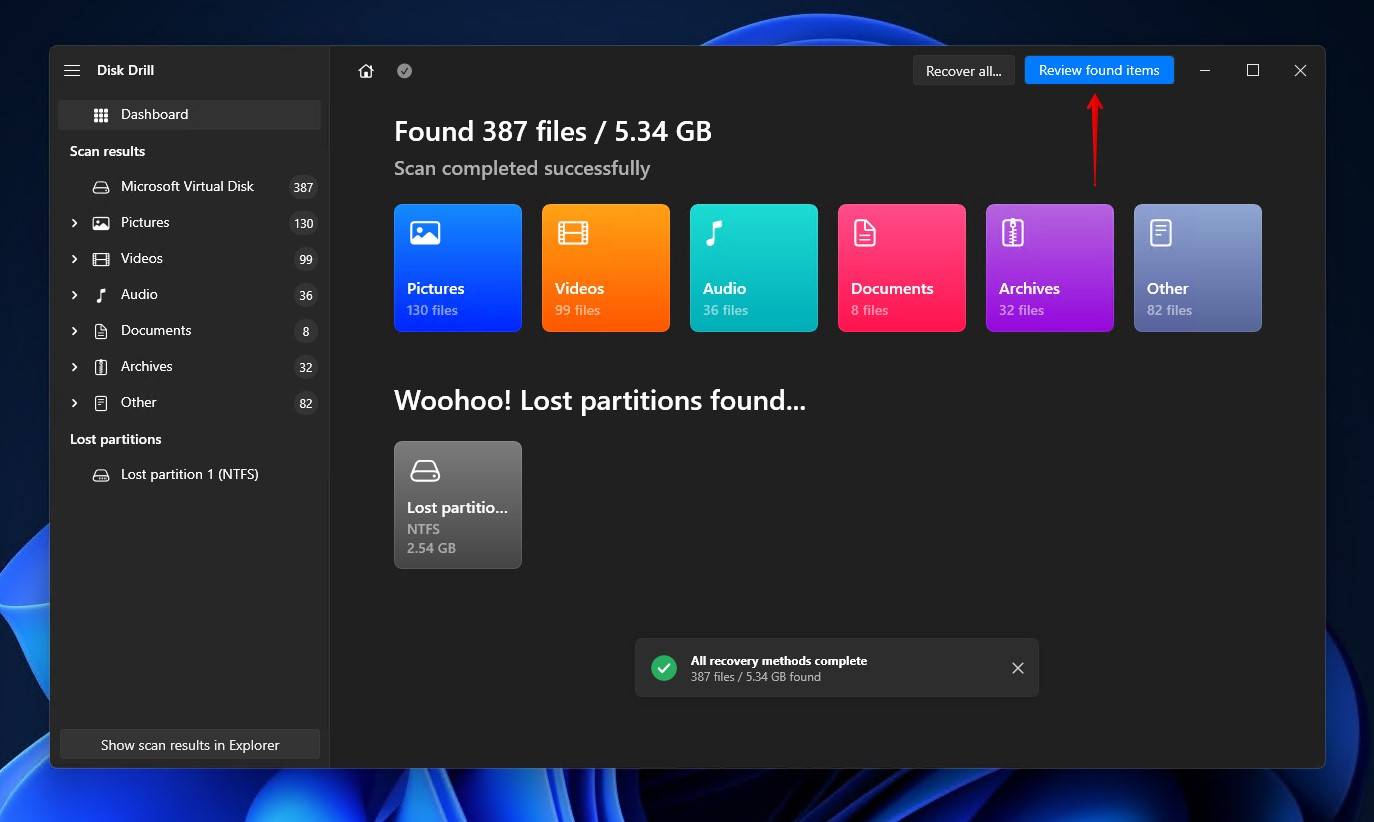
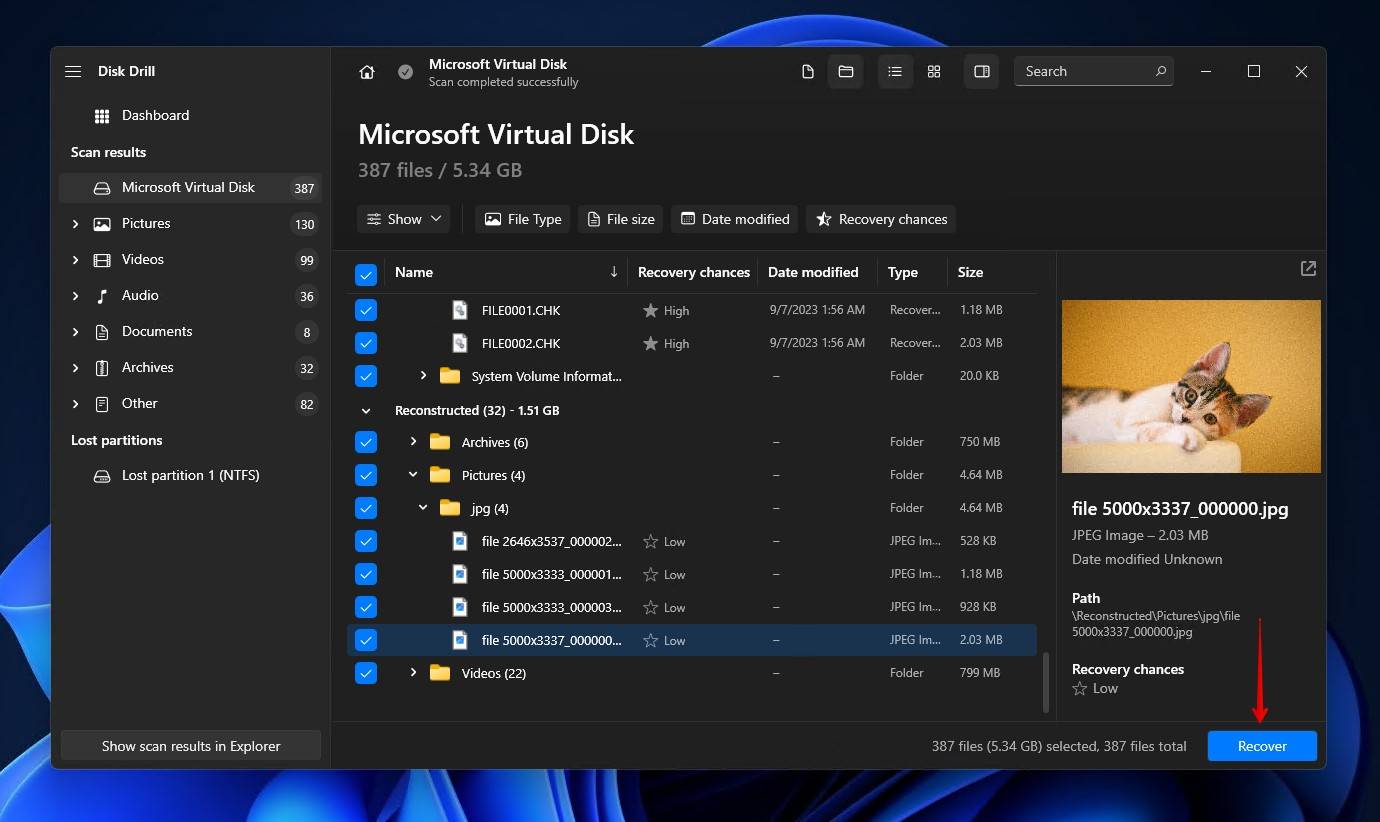
- Select the files you want to recover. The Recovery chances column gives you an indication of which data is recoverable and which is too damaged. When you’re ready, click Recover to proceed.
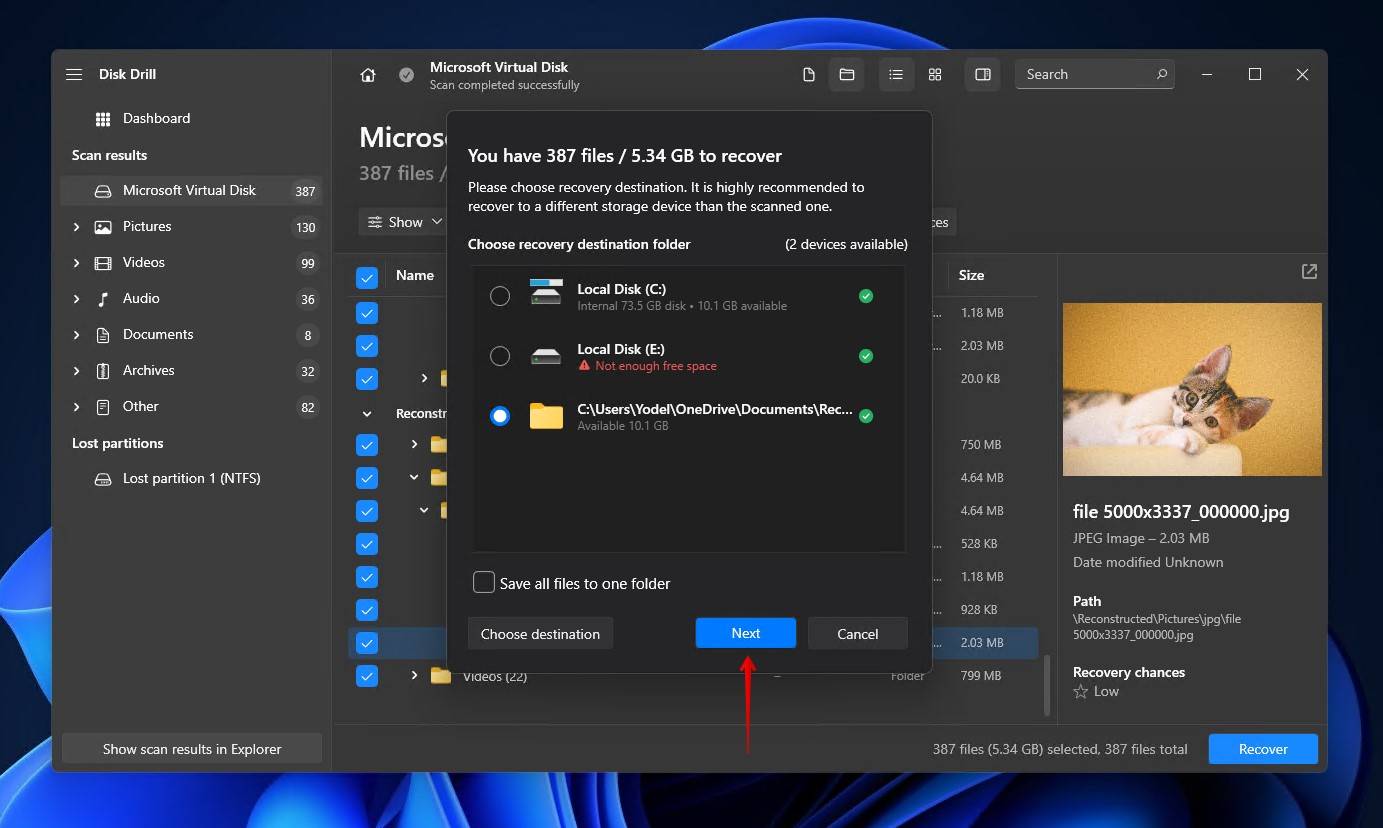
- Choose where you’d like to store the recovered files. It’s essential that you use a separate storage device to avoid corrupting the data during recovery. When ready, click Next.
You can learn more about Disk Drill as a data recovery tool in our Disk Drill review, where we explore its recovery abilities, usability, and safety to users. While Disk Drill is very useful, I understand that it’s not everyone’s cup of tea. Therefore, I recommend checking out some Disk Drill alternatives for additional recommendations.
Method 4: Decrypt Data Encrypted by Ransomware
When it comes to decrypting data encrypted by ransomware, you should look for a specialized decryption tool that has been created for the type of encryption used. No More Ransom has an extensive list of decryption tools you can explore, most of which have been created by leading companies in the cybersecurity space such as Trend Micro and Kaspersky Lab. All you need to do is find the decrypting tool for your specific type of ransomware and follow the how-to guide to regain access to your data.
Outside of specialist tools, there are also general ransomware decryptors like GIBON Ransomware Decryptor, but these don’t have a high rate of success as there’s no guarantee that they can treat the type of ransomware you’ve encountered.
Method 5: Fix the Damaged File System
Your data may still be present on the drive but merely inaccessible as your file system has become damaged or corrupted. Restoring your file system to a working state will also restore access to your encrypted files.
Software like TestDisk and DiskGenius are capable of scanning your file system and repairing any damage that is found, with the latter evidently being the perfect solution in a similar data loss case. There’s no telling what your odds of success are, but I would venture that it’s worth a shot if you know that the file system is corrupted.
Let me show you how to recover partitions that have been lost due to a corrupted file system with DiskGenius:
- Download and install DiskGenius.
- Right-click your disk and click Search Lost Partitions.
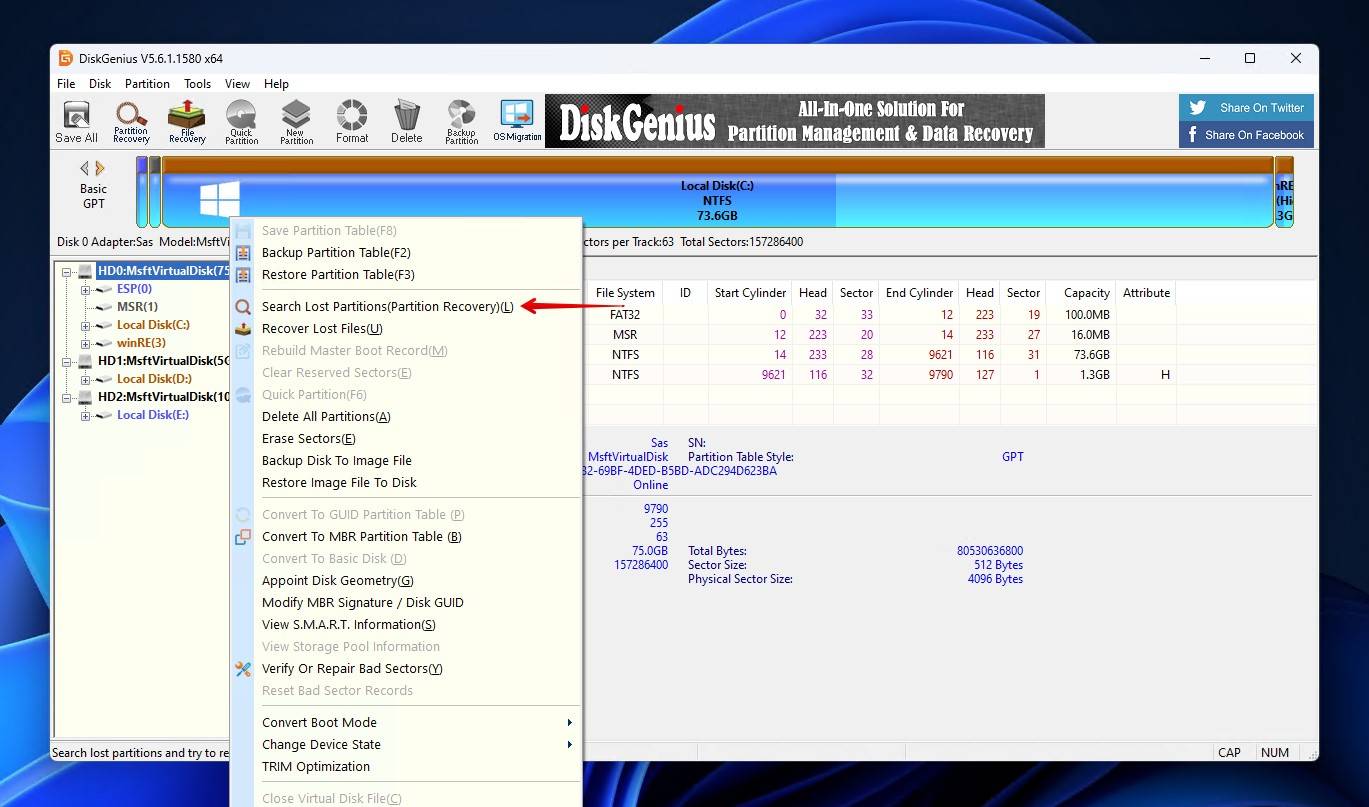
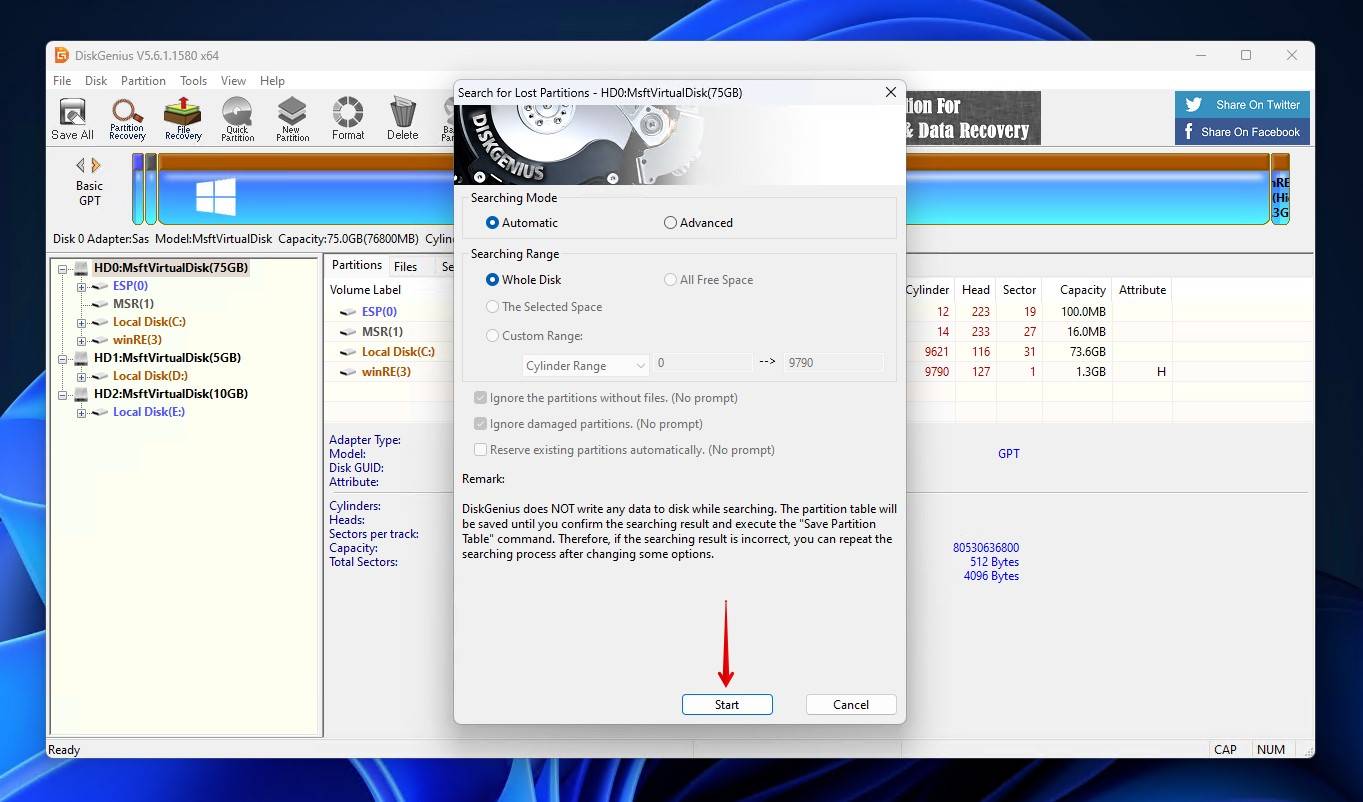
- Click Start.
- If your lost partition is found, you then have the option of writing it back to the partition table by clicking Disk, and then Save Partition Table. I highly recommend double-checking everything before writing the partition table.
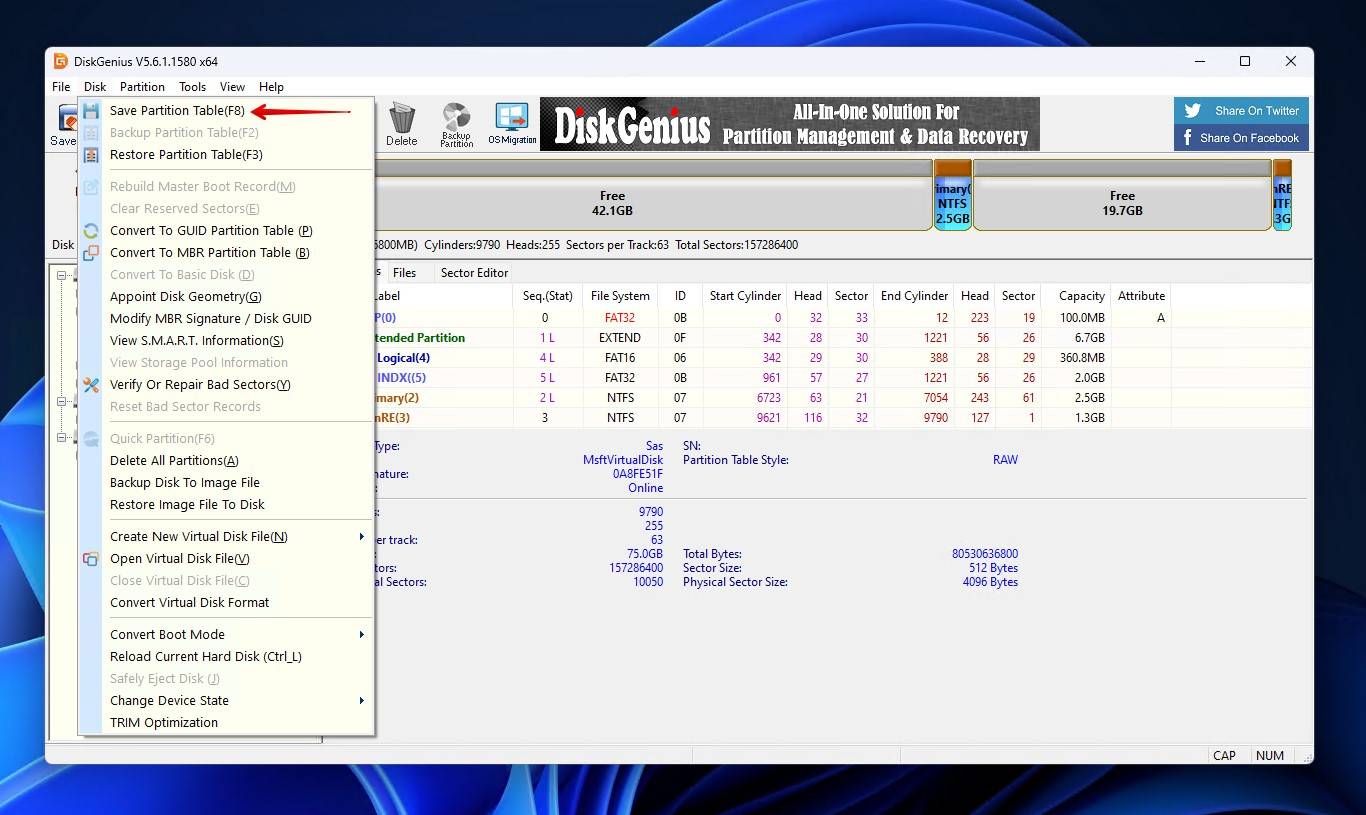
- Click Yes to confirm the action.
How to Prevent Encrypted Data Loss
I wouldn’t feel right if I didn’t close this article out with some tips on how to prevent the loss of encrypted data in the future. I know that some aspects of keeping your data safe can feel tedious at first, but just simple changes can be the difference between a 10-minute and 10-hour data recovery situation.
- 💾 Back up your data – Always keep multiple, up-to-date backups of your encrypted data. You don’t want to end up like this company that lost the vast majority of its data in a ransomware attack. All major operating systems have a backup utility baked in. The 3-2-1 rule is a reliable backup strategy, which involves maintaining 3 copies of your data across 2 different types of storage devices, with 1 being stored off-site.
- 💥 Replace failing hardware – Once a hardware component has started showing signs of failure, it will only get worse. And, there’s no telling how soon the problem will escalate. Rather than try to put off the imminent investment in a replacement part, do it now to minimize the risk of data loss, especially in the case of failing hard drives and SSDs.
- 🔑 Secure key management – Be sure to keep a backup of any certificates, security keys, or recovery codes needed for decryption. Personally, I prefer to store them in a password manager like LastPass or BitWarden for secure access from anywhere with an internet connection.
- 🦺 Practice good internet safety – In general, it pays to be extra cautious when browsing the internet. Just a few basic habits can help a lot. Download files from their original source, verify the sender’s address in emails, and always use antivirus. You can find more insights over at the National Cybersecurity Alliance.
Despite the added layer of complexity that encryption adds to data recovery, proactively taking care of your data minimizes the risk of data loss and ensures you have a quick recovery plan if everything goes south.
Conclusion
Data encryption, by its very nature, makes data difficult to recover and access if you don’t have the correct certificates, security keys, or credentials. Thankfully, if you do have the appropriate access, you can recover encrypted data that has been deleted.
The key to mitigating encrypted data loss lies in proactive prevention. If you haven’t already, make sure you set aside some time to create a comprehensive backup of your data.
FAQ
Can you recover encrypted data?
Yes, you can recover encrypted data. But, the necessary certificates or credentials are still required to access the data. Without them, you can recover the data, but won’t be able to use it.
Can encrypted data be recovered without a key?
You can recover data without a key, but that same data won’t be accessible without the key. Once recovered, it will still be in its encrypted form, resulting in no programs being able to open it.
Are there any free tools for encrypted data recovery?
There are plenty of free data recovery tools out there. A solution like Recuva can work, though it doesn’t offer the same level of recovery performance as paid alternatives. No matter what option you choose, it must be capable of finding data using file records, as signature-based recovery will not work.
How can I test if my encrypted files are recoverable?
You can do so by creating a byte-to-byte copy of the drive and recovering the data from that. This way, your original drive is left in its current state.
Can ransomware-encrypted data be recovered?
Yes, but there are never any guarantees. Websites like No More Ransom and Emsisoft contain a wealth of decrypting tools designed to target specific types of ransomware.
This article was written by Jordan Jamieson-Mane, a Staff Writer at Handy Recovery Advisor. It was also verified for technical accuracy by Andrey Vasilyev, our editorial advisor.
Curious about our content creation process? Take a look at our Editor Guidelines.
