Recently, a question was published in our community section about file signatures and their role in the data recovery process. While we addressed this query briefly in the forum, the complexity and importance of understanding what file signatures are and how they affect data recovery warrant a more thorough exploration. This comprehensive guide will equip you with the knowledge to grasp this vital concept and leverage it to potentially recover your precious data.
What Are File Signatures?
File signatures, also referred to as magic numbers, are unique identifiers that allow operating systems and software applications to recognize and classify specific file types. They consist of a fixed sequence of bytes at the beginning or end of a file, which can be viewed using a hex editor.
Think of a file signature as a sort of digital fingerprint; just as a fingerprint uniquely identifies a person, a file signature uniquely identifies the type of file, whether it’s a JPEG image, a PDF document, or an executable program.
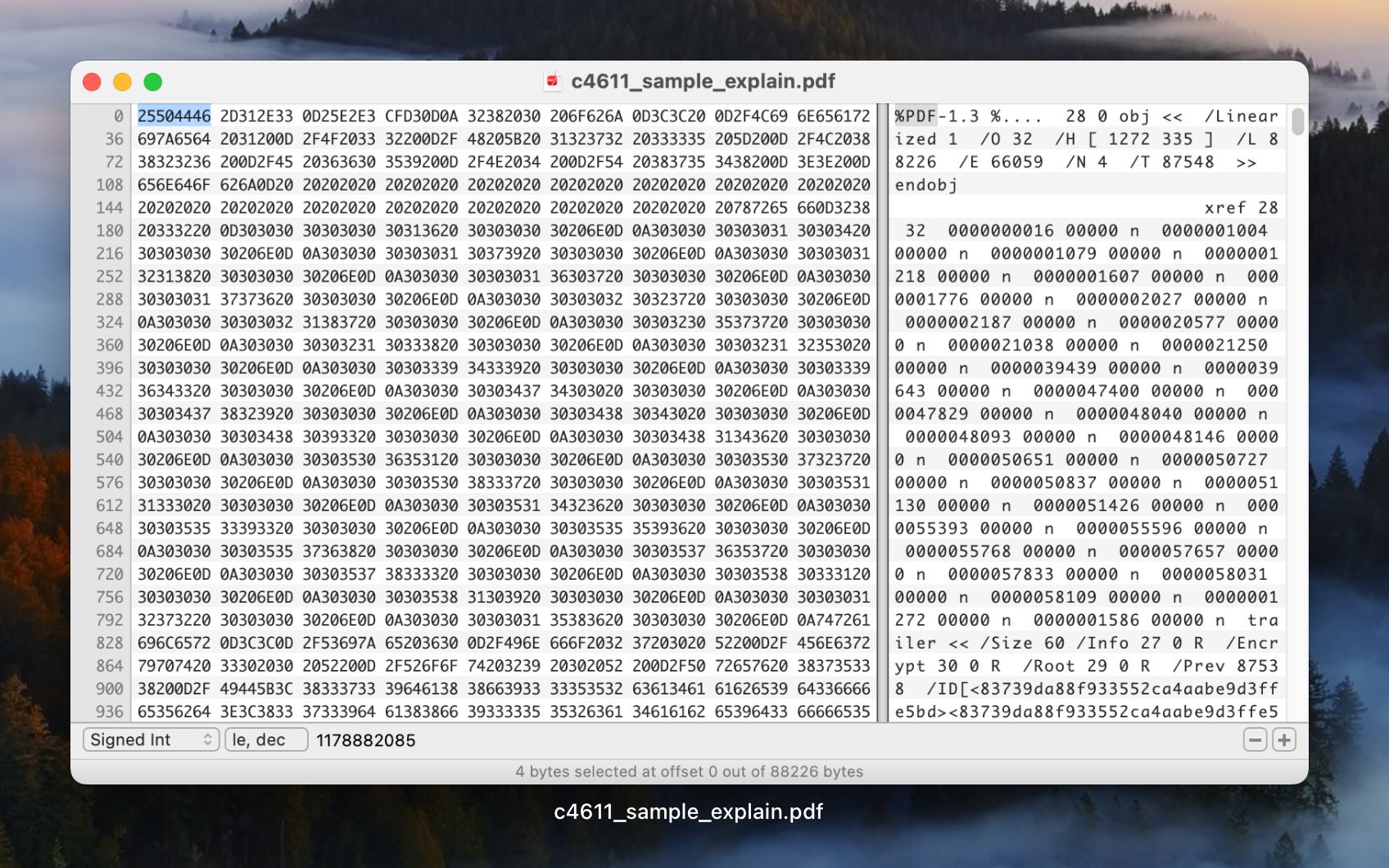
A hex editor showing the file signature of a PDF file.
The following table provides an overview of some of the most commonly used file formats, along with their signatures:
File Type |
Signature (Hex) |
File Format Description |
PDF Document |
25 50 44 46 |
Used for documents that include text, images, and other elements. |
JPEG Image |
FF D8 FF |
Commonly used for digital photography and web images. |
PNG Image |
89 50 4E 47 0D 0A 1A 0A |
Preferred for web graphics due to transparency support. |
GIF Image |
47 49 46 38 37 61 |
Supports animations; used for simple graphics on websites. |
BMP Image |
42 4D |
Bitmap image file, a raster graphics image file format used to store digital images. |
ZIP Archive |
50 4B 03 04 |
Compression format widely used for data compression and archiving. |
RAR Archive |
52 61 72 21 1A 07 00 |
Another popular compression format offering strong compression. |
MPEG Video |
00 00 01 BA |
Used for MPEG videos on DVDs and other digital video platforms. |
AVI Video |
52 49 46 46 xx xx xx xx 41 56 49 20 |
Audio Video Interleave format, stores video and audio data combined. |
MP3 Audio |
FF FB |
Audio format widely used for music files thanks to its compression. |
Adobe Photoshop Document |
38 42 50 53 |
PSD files used for storing Adobe Photoshop project files. |
Knowing these signatures can be useful in a variety of situations, such as when you’re analyzing a suspicious file to determine its true purpose or, as we explore in this article, when you’re trying to recover lost or deleted files.
How Are File Signatures Used in Data Recovery?
When a file is lost or accidentally deleted, recovering it often depends on the ability to identify its file signature through a process known as file carving.
File carving is a forensic technique used to recover files based solely on their intrinsic data, without any reference to an underlying file system. This method involves scanning a data storage medium—like a hard drive or a memory card—directly for known file signatures.
The success of file carving depends on several factors, including the type of file, the size of the file, and the level of fragmentation. In some cases, file carving may only be able to recover fragments of files. However, even partial file recovery can be valuable, as it may allow you to salvage some of your lost data.
File carving is particularly useful in situations where the file system has been damaged or corrupted, or where files have been deleted or lost without any record of their previous location. For example, Breeuwsma et al. (2007) have used file carving to search through data from flash memory that couldn’t be directly translated to the file system level. In this case, the authors were looking for audio and video files in a mobile phone’s flash memory.
In practice, file carving is typically used in conjunction with other data recovery techniques, such as file system-based recovery, which relies on the file system’s records to locate and recover lost or deleted files.
How to Recover a Lost File Based on Its File Signature?
In theory, you could recover lost files using just a hex editor and your knowledge of file signatures. The process would go like this: open your drive in the hex editor, scroll through billions of hexadecimal values, spot a familiar pattern like 89 50 4E 47 0D 0A 1A 0A (a PNG image), then manually copy everything from that point until you hit the file’s end. Sounds doable, right?
Wrong. This method is like trying to find a specific snowflake in an avalanche—theoretically possible, but practically insane. A typical 1 TB drive holds about a trillion bytes. Scanning that much data by eye, recognizing patterns, and manually extracting files? You’d need several lifetimes, superhuman focus, and probably a lot of coffee.
Thankfully, modern data recovery software can perform signature-based recovery automatically, turning this Sisyphean task into a few simple clicks. Here are several popular data recovery solutions and their capabilities:
Data Recovery Software |
Number of Supported File Signatures |
Recovery Types |
Custom Signatures |
Disk Drill |
~400 |
File System & Signature |
No, but you can request new types here. |
Recuva |
~100 |
File System & Signature |
No |
PhotoRec |
~500 |
Signature |
No |
R-Studio |
500+ |
File System & Signature |
Yes |
Windows File Recovery |
~50 |
File System & Signature |
No |
As you can see, most data recovery solutions combine signature-based recovery with file system-based recovery.
The combined approach offers the highest chances of recovering your data. File system-based recovery utilizes the file system’s records to locate deleted files, often restoring the original filenames and folder structure. On the other hand, signature-based recovery digs deeper, finding files even when the file system is damaged, but without their original names and locations.
There are exceptions, though. PhotoRec, for example, focuses solely on signature-based recovery. This laser focus allows it to support a vast number of file formats, making it a powerful tool for recovering data from heavily damaged storage devices. However, it will never be able to recover filenames or folder structures.
Since there are more file formats in the world than any single developer could possibly implement, some applications, like R-Studio, let users add custom signatures. This process looks something like this:
- Identify the file signature: Start with intact files of the same type you want to recover. Using your favorite hex editor (R-Studio comes with one), compare the files to find a consistent pattern at the beginning and/or end of the files, which is your file signature.
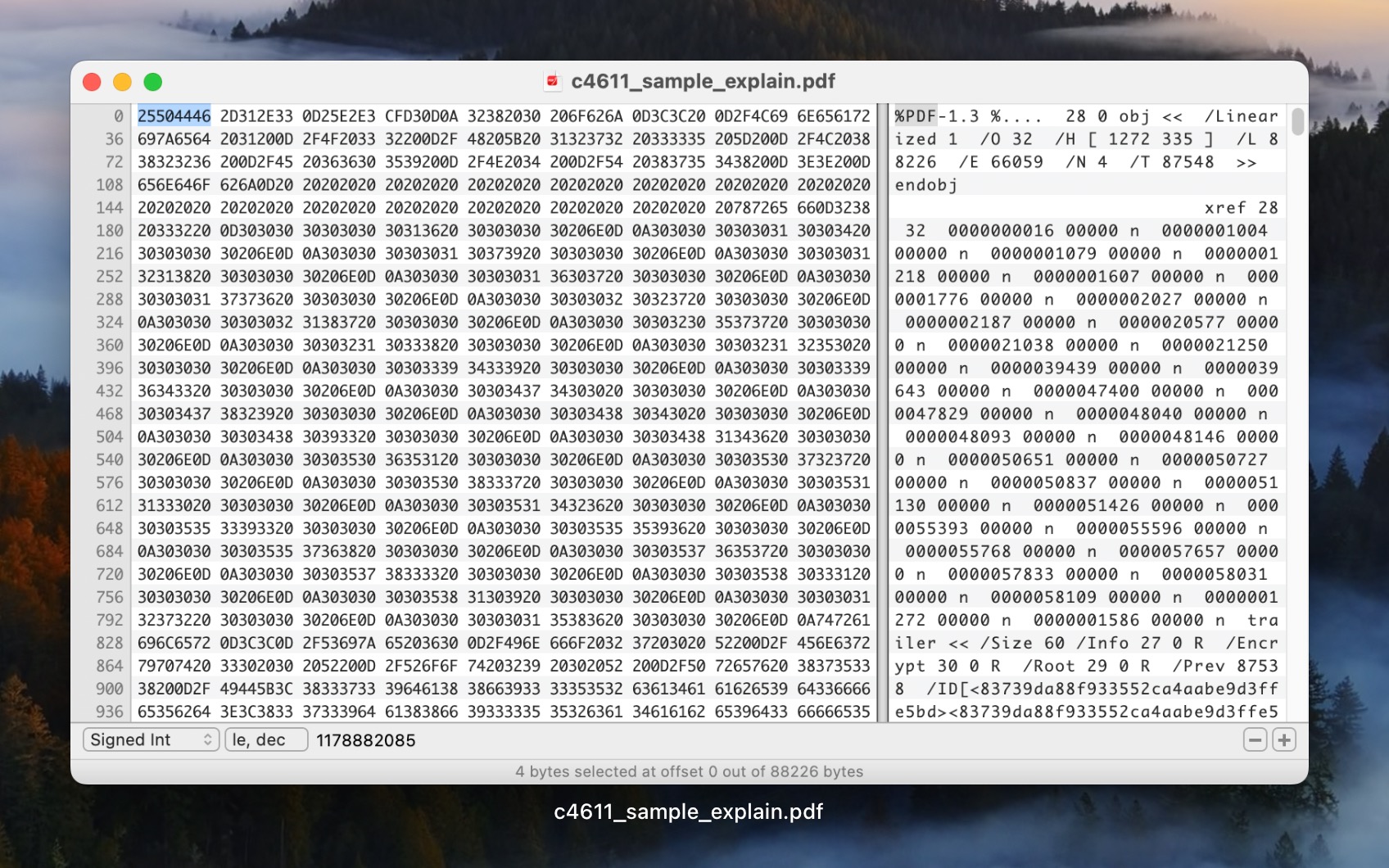
- Create a new file type in your data recovery software: Define a new file type in your data recovery software’s settings. You’ll provide details such as a unique ID, description, and the file signature in hexadecimal format.
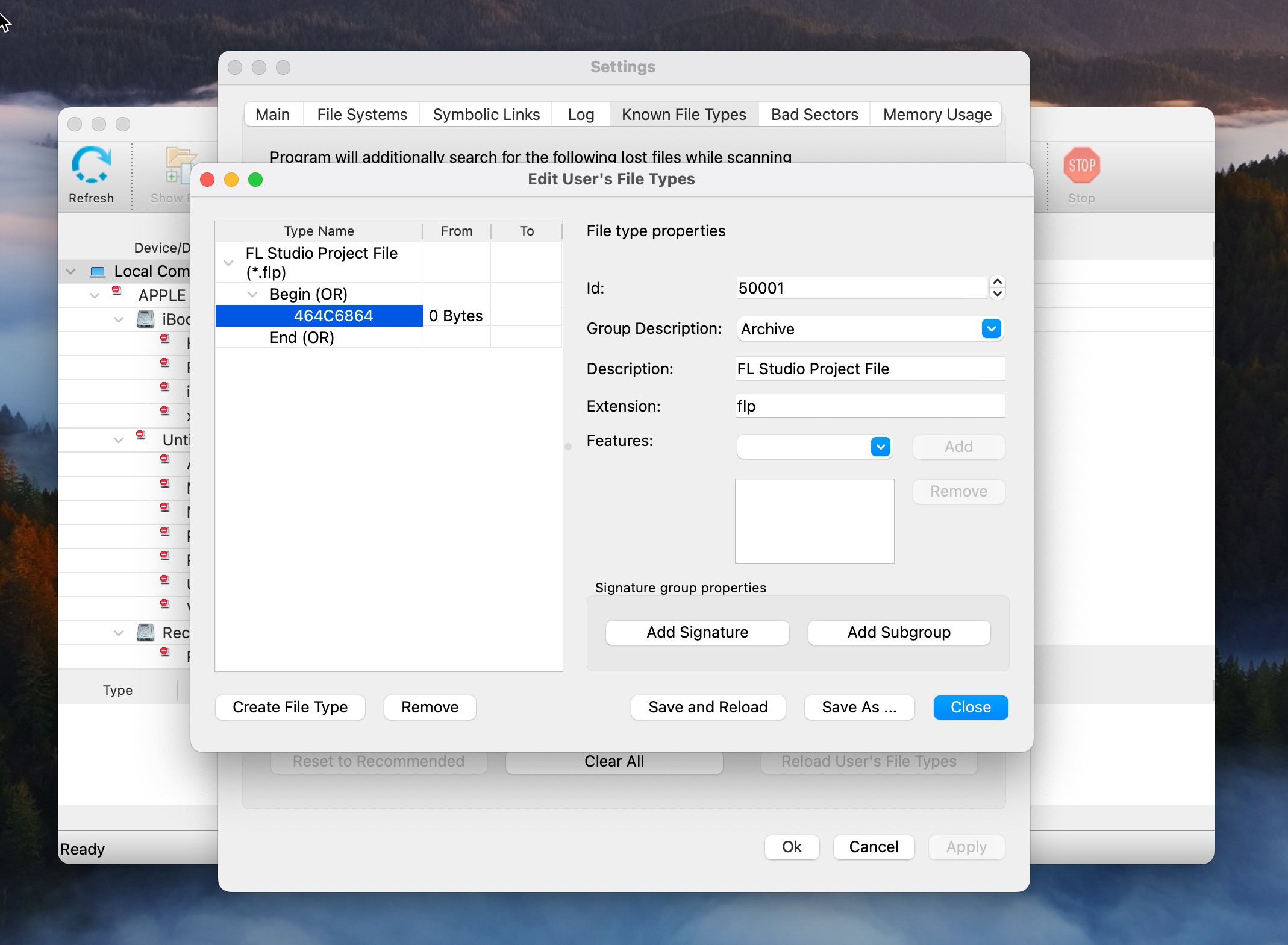
- Use the custom file type for scanning: Once your custom file type is defined, you can use it to scan for lost files that match this signature.
The ability to add and recover custom file signatures is indispensable when dealing with proprietary file formats that no data recovery software can possibly support right out of the box.
Signature-Based Recovery Has Its Limits
File signatures and the above-demonstrated signature-based recovery process can save the day and turn many desperate data loss situations around, but they have their limits.
The biggest issue—one we’ve already mentioned in this article briefly but whose importance can’t be stressed enough—is that it’s not possible to recover filenames and file paths while relying solely on signatures. That’s because this information is stored in the file system, not the file itself. If the file system If the file system is corrupted or overwritten, signature-based recovery will still find your files, but they will have random names assigned to them by the recovery software.
Remember those signatures we showed you earlier, such as FF D8 FF (JPG) or 00 00 01 BA (MPEG video)? Well, it’s easily possible for a random part of a file, such as a small region of a photo, to include these same exact sequences of bytes. This can confuse less capable data recovery software and lead to false positives. The software will recover what looks like a legitimate file, but the file will be impossible to open, and you might easily waste hours trying to make it work.
Another limitation of signature-based recovery has to do with fragmentation. Modern operating systems and storage devices store data in non-contiguous blocks across the drive. Normally, this results in optimized storage space utilization and performance, but it can jeopardize your chances of success when recovering a file based on its signature because the signature indicating the start of the file may be located on a completely different part of the storage device than the signature indicate the file’s end.
Last but not least, it’s worth pointing out that—just like all other recovery methods that don’t involve cutting-edge exploits—it’s not possible to recover data based on its signatures from an encrypted storage device that you can’t unlock. Until decrypted, such data is nothing but random gibberish to any recovery tool.
This article was written by David Morelo, a Staff Writer at Handy Recovery Advisor. It was also verified for technical accuracy by Andrey Vasilyev, our editorial advisor.
Curious about our content creation process? Take a look at our Editor Guidelines.